| **User Account Status** | **Description** |
| [](https://docs.safedns.com/uploads/images/gallery/2022-08/d56P0mpNMPVj6QLl-2-user-tree.png) | The user has completed the authorization procedure and has been granted internet access. |
| [](https://docs.safedns.com/uploads/images/gallery/2022-08/pZOamG9xaWeQyB6h-3-user-tree.png) | Authorization restriction has been set in the [**User Settings**](https://docs.safedns.com/books/42-setup-users/page/configuring-users). |
| [](https://docs.safedns.com/uploads/images/gallery/2022-08/0L2I5ioKf4UcAmF7-4-user-tree.png) | The user has not completed the authorization procedure and has not been granted internet access. |
| **Symbol** | **Description** |
| [](https://docs.safedns.com/uploads/images/gallery/2022-08/YAq39FQWhGYv3O9i-1-user-management.png) | Create user account |
| [](https://docs.safedns.com/uploads/images/gallery/2022-08/K4pymhc1B8JwLDdK-2-user-management.png) | Create group |
| [](https://docs.safedns.com/uploads/images/gallery/2022-08/VcIEe1oXa8mxAWwy-3-user-management.png) | Delete user account or group |
**Login** must be entered in lowercase Latin characters, for example, j.smith
Recommendations for creating password complexity: minimum length - 10 characters; use of lowercase and uppercase Latin characters; use of numbers and special characters. You can generate a password.
When you fill in the **Additional settings**, a corresponding rule will be created in the user card in the **IP and MAC authorization** tab and in the **Authorization -> IP and MAC authorization** section. If this IP address or MAC address is used in DHCP server rules, then the **[DHCP server](https://docs.safedns.com/books/45-setup-services/page/dhcp-server)** rule will be in priority.
For accounts imported from MS Active Directory (AD), password verification is carried out by means of AD. Active Directory user authorization is configured in the corresponding [**section**](https://docs.safedns.com/books/42-setup-users/page/active-directory-user-authorization). You cannot create a user in the Active Directory group from SafeUTM. If you need to add an additional user to the Active Directory group, you must do so in the user tree on the domain controller.It is impossible to view or restore the account password, only changing is allowed.
After you have entered all required parameters, click **Save**. An account will be created that will automatically get all the values of some parameters of the group in which it was created. ---You can find the information about how to set up traffic quotas in the [**User Quotas**](https://docs.safedns.com/link/72#bkmrk-setting-up-user-and-) section.
--- ##### IP and MAC Authorization category This category contains authorization rules by IP and MAC created for a specific user in two sections: - Users -> User & Group -> IP and MAC authorization [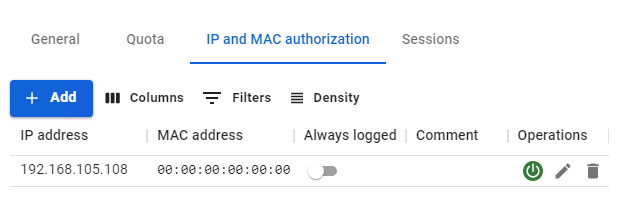](https://docs.safedns.com/uploads/images/gallery/2022-08/cwZqCgl3wiXfYQTx-4-configuring-users.png) - Users -> [**Authorization** ](https://docs.safedns.com/books/42-setup-users/page/user-authorization)-> [**IP and MAC authorization**](https://docs.safedns.com/books/42-setup-users/page/authorization-by-ip-and-mac-address)[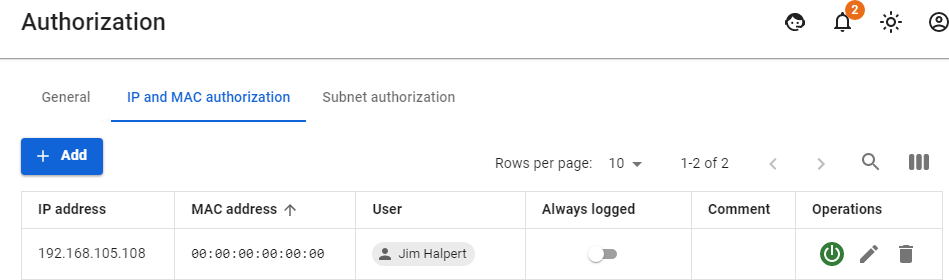](https://docs.safedns.com/uploads/images/gallery/2022-08/OFQ7FbgGwlR14rSt-5-configuring-users.png)The **IP and MAC authorization** rules also create a similar binding in the SafeUTM [**DHCP server**](https://docs.safedns.com/books/45-setup-services/page/dhcp-server). But if the same IP and MAC addresses are used in enabled DHCP server rules, then the DHCP server rules will be executed first.
--- ##### Sessions category Contains a table with information about all active user sessions: [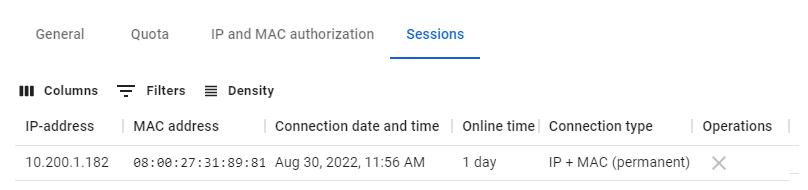](https://docs.safedns.com/uploads/images/gallery/2022-08/V1ipEba0PDvB06gB-6-configuring-users.png)When you click on "X" in the **Operations** column, UTM will terminate the user's session. A similar table is located in the **Monitoring** -> [**Authorized users**](https://docs.safedns.com/books/43-setup-monitoring/page/authorized-users-and-vpn-users) section. # Terminal Server Users Used for remote work with the provision of a separate desktop for each user. Provides a service for the work of dozens and even hundreds of users. --- #### Terminal Server Authorization If the admin does not need the separate authorization of terminal server users, and the same access settings (content filtering and user firewall) can be applied to them, the server can be authenticated as a single user. The best option is [**authorization by IP address**](https://docs.safedns.com/books/42-setup-users/page/authorization-by-ip-address). Please note that when the number of users on the terminal server is large, it may be necessary to [**increase the number of simultaneous sessions**](https://docs.microsoft.com/en-us/windows-server/remote/remote-desktop-services/troubleshoot/remote-desktop-service-currently-busy#check-the-connection-limit-policy) from one address in advanced security settings. --- #### Authorization of Terminal Server Users **Separate authorization of terminal server users** (running under Windows Server 2008 R2 and Windows Server 2012 OS) is possible using [**SSO (NTLM)**](https://docs.safedns.com/link/50#bkmrk-web-authorization-%28s). In such a case server authorization by IP is not necessary. For separate authorization of terminal server users, [**Remote Desktop IP Virtualization**](https://docs.microsoft.com/en-us/troubleshoot/windows-server/remote/remote-desktop-ip-virtualization) must be configured on the terminal server, and user authorization via web authorization (SSO or NTLM) must be configured on the SafeUTM server. Authorization of terminal server users based on logs of the AD domain controller has not yet been implemented. ---Keep in mind, that the operating system itself can also generate traffic (for example Windows telemetry) without user intervention. Because of this, the timeout for the user will be constantly reset and will not be able to function correctly.
You can change the time of automatic logout using the settings **Disconnection timeout** by going to **Users -> Authorization**: [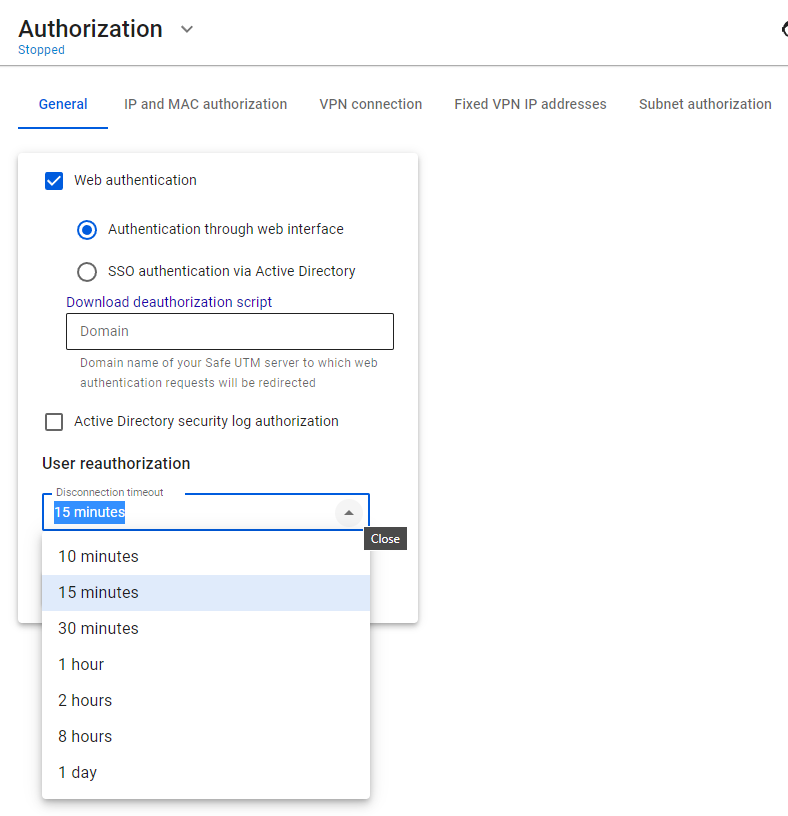](https://docs.safedns.com/uploads/images/gallery/2022-08/yV71Dl3RJbFl42rA-1-user-authorization.png)For the new timeout to be applied, you need to reboot SafeUTM.
Supported browsers: - Google Chrome, version >= 76 - Firefox, version >= 71 - Safari, version >= 13
In this type of authorization, any request from an unauthenticated user sent via a web browser will be redirected to a special authorization page of SafeUTM. After successful authorization, you will be redirected to the specified request. For this type of authorization, the user must have the IP address of the SafeUTM local network interface specified on the network card as a gateway (chained into a gateway chain) or for direct connections to a proxy. Also, before connecting to the Internet, the **DNS resolution of addresses** must work, otherwise, the browser request to the *example.com* address will not be redirected to the gateway and the username and password request will not appear in the browser. You can check name resolution in Windows using the command: `nslookup google.com`. The output of this command must contain IP addresses. To configure authorization via the web interface, go to **Users -> Authorization** and select **Web authentication** and **Authentication through web Interface**, as shown in the screenshot below: [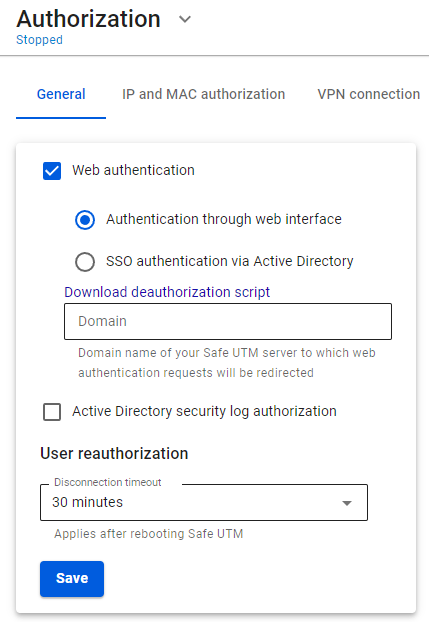](https://docs.safedns.com/uploads/images/gallery/2022-08/NeXha5XywKwxEH77-1-web-authorization.png) After filling in the **Domain name** field and saving the settings, a Let’s Encrypt certificate will be issued and the user will be redirected to the authorization window, bypassing the security exception page: [](https://docs.safedns.com/uploads/images/gallery/2022-08/ofe14Y0IYXoNIkYu-2-web-authorization.png) If a certificate for such a domain has already been loaded in the [**Certificates**](https://docs.safedns.com/books/45-setup-services/page/tls-certificates) section, then it will be used and a new certificate will not be issued. Next, try to access the internet via a web browser. An authorization window should appear where you need to type in the account’s login and password of the user created on SafeUTM. The authorization window can be seen in the screenshot below: [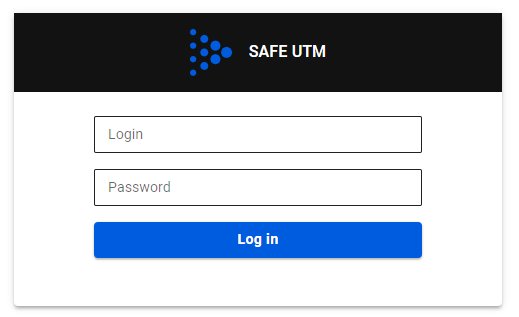](https://docs.safedns.com/uploads/images/gallery/2022-08/GU3aj0yMe7hszIZk-3-web-authorization.png)When the user is authenticated via the web, access to the internet will be provided until the authorization is forcibly canceled or terminated due to the user’s inactivity.When logging into an HTTPS website, the user must confirm the trust of the SafeUTM certificate. Alternatively, the certificate can be added to trusted root certification centers on the device (for example, through domain policies).
It is recommended to specify the IP address of the local SafeUTM as a DNS server on the LAN computers and devices.
The **IP and MAC authorization** rules also create a similar binding in the SafeUTM [**DHCP server**](https://docs.safedns.com/books/45-setup-services/page/dhcp-server). However, if the same IP and MAC addresses will be used in the enabled rules of the DHCP server, then the DHCP server rules will be executed first.
To configure IP and MAC authorization, you must: 1. In section **Authorization -> IP and MAC authorization** click **Add**. 2. Create an **IP and MAC authorization binding rule:** [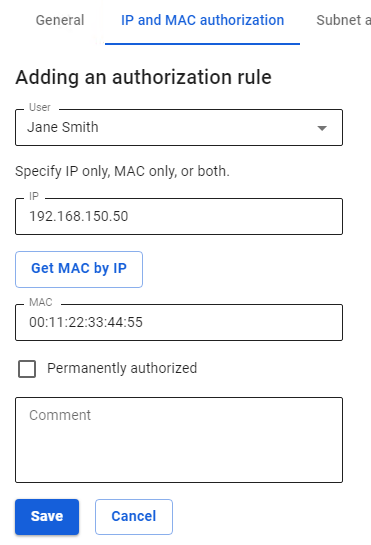](https://docs.safedns.com/uploads/images/gallery/2022-08/ndHdfngwCyv36zM8-1-authorization-by-ip-and-mac-address.png)Set the flag **Permanently authorized** to provide unlimited internet connection even if the user is not active. The rules created in this section are reflected in the [**user card**](https://docs.safedns.com/books/42-setup-users/page/configuring-users). Find out more about user authorization only by IP address or MAC address in the articles [**Authorization by IP address**](https://docs.safedns.com/books/42-setup-users/page/authorization-by-ip-address) and [**Authorization by MAC address**](https://docs.safedns.com/books/42-setup-users/page/authorization-by-mac-address)
# Authorization by IP address #### Configuring Authorization by IP Authorization by IP implies that an authorized user will gain access to Internet resources without entering a username and password, but simply by initiating a connection to these resources. You can also authorize network devices (such as CCTV cameras, network printers, etc.) that are located in broadcast domains other than SafeUTM, and that require Internet access.If the device is a router and SNAT is enabled on it, then when its external IP is authorized in UTM, all users behind this router will gain Internet access. Users who are behind the router in the local UTM network cannot be authorized using the IP address - MAC address bind, since the router does not handle L2-level traffic. If authorization by IP address is configured, this IP will not be issued by [**DHCP**](https://docs.safedns.com/books/45-setup-services/page/dhcp-server).
To authorize a user by IP address: 1\. [**Create**](https://docs.safedns.com/books/42-setup-users/page/user-group) a user that will be authorized by IP in SafeUTM or [**import**](https://docs.safedns.com/books/42-setup-users/page/import-of-users) a user from Active Directory. 2\. Go to **Users -> Authorization -> IP and MAC authorization.** 3. Create a binding rule **IP address <--> User**, as shown in the screenshot. [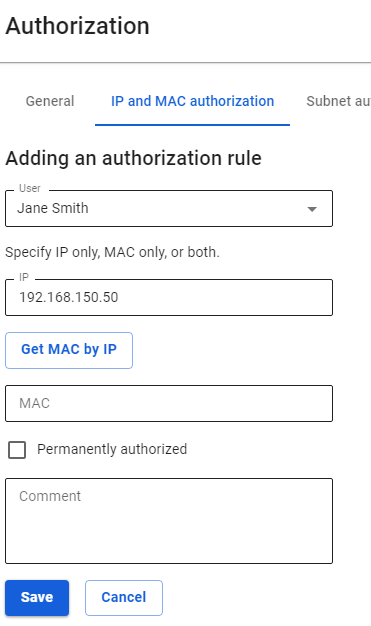](https://docs.safedns.com/uploads/images/gallery/2022-09/Akmr4vM2GraPuJZ4-1-authorization-by-ip-address.png)The user's IP address is to be used when creating a session. The computer/device's IP address must match the one specified in the rule.
If the user is network equipment (video cameras, servers, etc.), it is recommended to select **Permanently Authorized**, in which case the user session will be created after the UTM is turned on, and the network equipment does not need to make a web request. For such equipment, it is recommended to configure a static IP address or DHCP with an IP address binding. This is required, for example, for resources [**published via DNAT**](https://docs.safedns.com/books/49-setup-publishing-resources/page/portmapping-port-forwarding-dnat).
After the user makes a web request, a session with the IP authorization type will automatically be created on UTM in **Monitoring -> Authorized Users**. [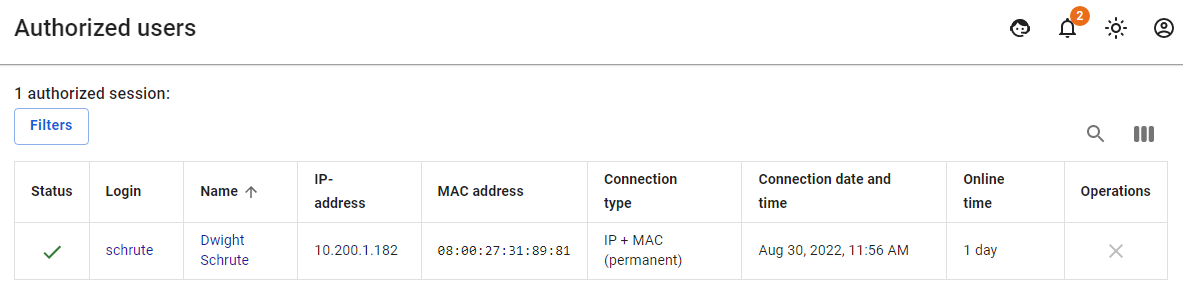](https://docs.safedns.com/uploads/images/gallery/2022-08/ENGZbRvIuoX11Gdk-2-authorization-by-ip-address.png)For sessions with an IP authorization type, the **MAC address** field is not filled in, because, with this type of authorization, there is already an IP address required to create an authorization session.
You can use device search to automatically create users when they try to access the Internet. To do this, see the [**Netscan**](https://docs.safedns.com/books/42-setup-users/page/netscan) article.
Only one device can be authorized under one user by IP address (simultaneously with this type of authorization, two more devices can be authorized under one user by any other authorization method). --- #### Adding Group of Devices with Authorization by IP You can add users from a range of IP addresses (for example, a network distributed by access points to wireless devices over Wi-Fi). To do this, you need to follow these steps: 1. Create a new group in the user tree. 2. Select a group from the user tree to which you want to add devices. 3. In the **General** tab, click **Create Users**. A window opens with the settings of the users created. Fill in the following fields: 1. **Name Prefix.** Users will be created with names of the type "User IP address ". 2. **Login prefix.** Users will be created with logins of the type "user\_ip-address ". 3. **IP addresses of the first and last users. [](https://docs.safedns.com/uploads/images/gallery/2022-09/XtzMNoTcEvAK9W9n-3-authorization-by-ip-address.png) [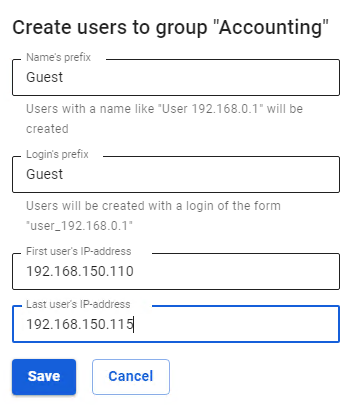](https://docs.safedns.com/uploads/images/gallery/2022-08/sAsj6Ts5BZdEoF5Q-4-authorization-by-ip-address.png)[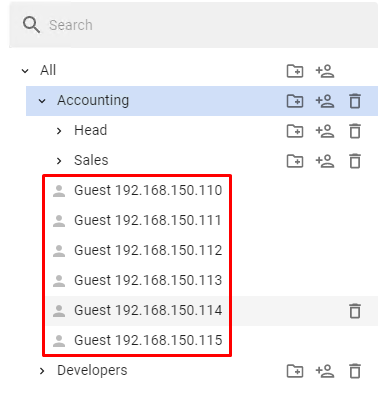](https://docs.safedns.com/uploads/images/gallery/2022-08/2MHpvp5MOTHVifln-5-authorization-by-ip-address.png)**If some IP addresses from the range are already used by other SafeUTM users, they will be skipped during creation, and as a result, fewer users will be created than addresses in the range.
Users will be created with the settings of the created group and an IP address from the range. In addition to the user tree, in the section **Users -> Authorization -> IP and MAC authorization** for each user, a binding rule **IP address <--> User** will be created automatically, as shown in the screenshot: [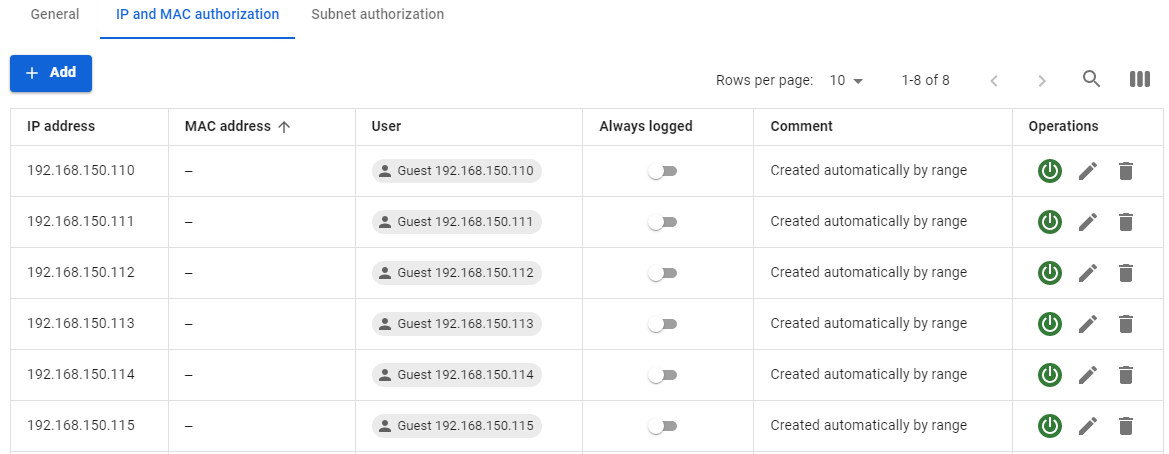](https://docs.safedns.com/uploads/images/gallery/2022-08/4SpdTA5gQWOdxypH-6-authorization-by-ip-address.png)If you use IP authorization with static binding in DHCP, it is preferable to transfer such rules to [**authorization by MAC address**](https://docs.safedns.com/books/42-setup-users/page/authorization-by-mac-address).
# Authorization by MAC address This type of authorization is suitable for those devices whose location changes from time to time between local networks within the organization (for example, employees' work laptops) or network devices that are issued an IP address via DHCP, on which IP+MAC binding is not configured.In order for a device to be authorized on UTM by MAC address, they must both be in the same broadcast domain, and UTM serves as the gateway for the devices.
Users who are behind the router in the local UTM network cannot authorize by MAC address, since the router breaks broadcast domains and does not process L2-level traffic. Such users can authorize only by IP address.
--- #### Configuring MAC Authorization To authorize a user by MAC address, you need to do the following: 1\. You need to find out the MAC address of the device. To do this, in the Windows command prompt, type the command: `ipconfig /all | findstr Address` [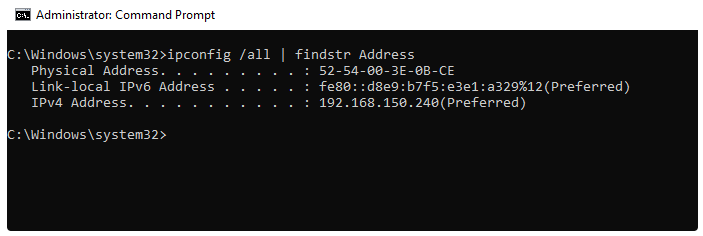](https://docs.safedns.com/uploads/images/gallery/2022-08/e6QoVqKdIYUjiDLC-1-authorization-by-mac-address.png) 2\. Make sure that the computer and UTM are in the same broadcast domain. To do this, on UTM in Server Management -> Terminal section, enter the command: `ip neigh` [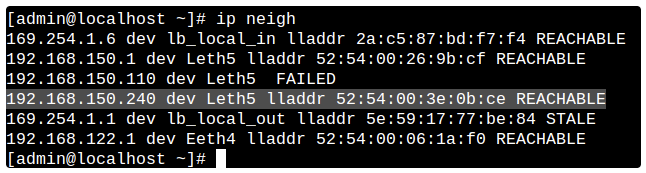](https://docs.safedns.com/uploads/images/gallery/2022-08/oIGtaChQyAaVNEnH-2-authorization-by-mac-address.png)This command outputs the UTM's ARP table, and the presence of an entry with the device MAC address and REACHABLE status indicates L2 availability between UTM and the device.
3\. Create a binding rule **User <--> MAC address** in **Users -> Authorization -> IP and MAC authorization:**It is not possible to set up permanent authorization for MAC authorization. This is technically impossible because an IP address is required to create an authorized session. Therefore, it is recommended to use MAC authorization in combination with a [**DHCP server**](https://docs.safedns.com/books/45-setup-services/page/dhcp-server).
The result can be viewed in **Monitoring -> Authorized users**, where a session with the MAC authorization type will be displayed. [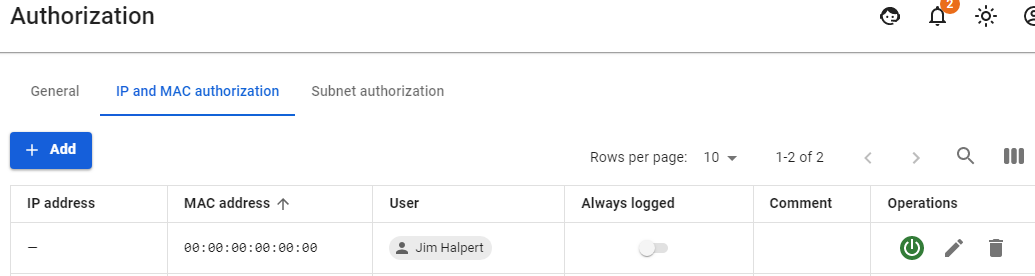](https://docs.safedns.com/uploads/images/gallery/2022-08/03xON6PEKqqEWCwW-3-authorization-by-mac-address.png) --- #### MAC authorization behavior when moving a device between local networks In organizations, there is often a situation when it is necessary to move between local networks with a laptop and at the same time always stay online. In such cases, authorization by MAC address works perfectly well.You must have your own DHCP server configured or on SafeUTM. In the distributed credentials, the gateway should be the local SafeUTM interface.
Let's take as an example a situation where a user `Dwight Schrute` needed to move with a laptop between local networks: - There are local interfaces configured on UTM as follows: [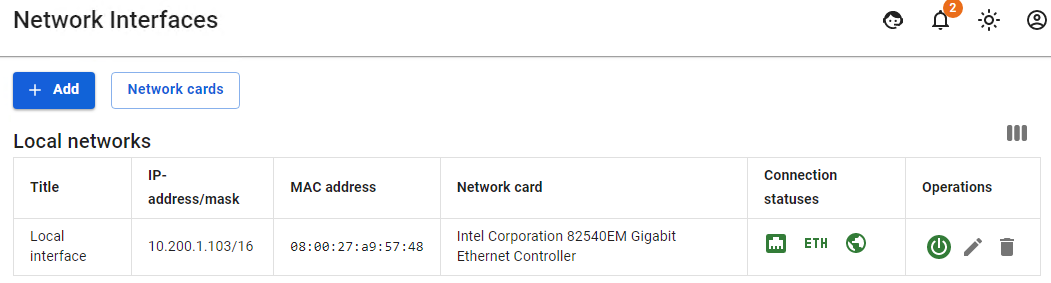](https://docs.safedns.com/uploads/images/gallery/2022-08/Wm7sPFl032kbtAxf-4-authorization-by-mac-address.png) - This user has a MAC address authorization rule configured: [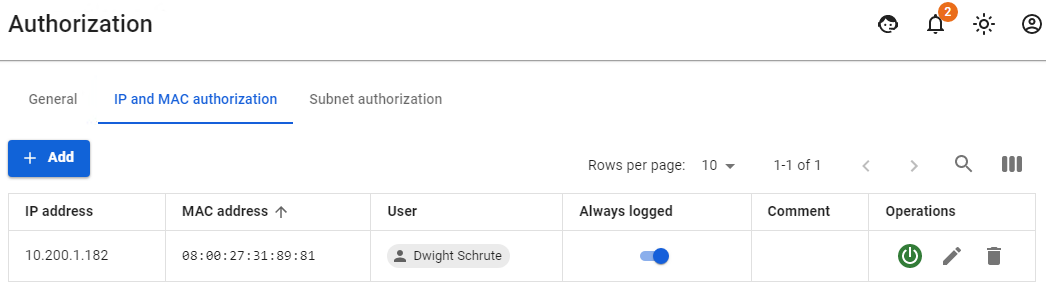](https://docs.safedns.com/uploads/images/gallery/2022-08/2Zt4TdxYs3HeNBs6-5-authorization-by-mac-address.png) - He also has one active session in the **Authorized Users** section: [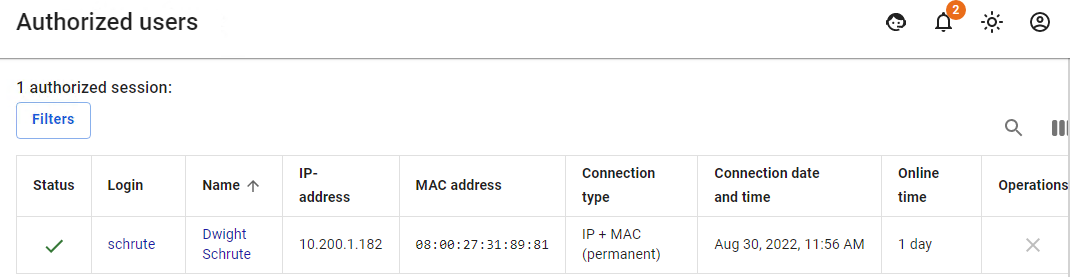](https://docs.safedns.com/uploads/images/gallery/2022-08/f09GVblLOFHrmc1d-6-authorization-by-mac-address.png) - Then the user moves from one local network to another. He is given other network credentials from the DHCP server, in which UTM is specified by the gateway, and if any activity on the part of the user is detected, the second session with authorization by MAC address will appear.If the user does not have access and can’t see the second session with authorization by MAC address, then most likely this could have happened due to the fact that the user's network credentials were not updated. Reset the old network credentials from the DHCP server and get new ones using the command: `ipconfig /release && ipconfig /renew`.
--- #### Configuring MAC Address Authorization for Network Printer and Other Network DevicesNetwork printers and other network devices that need access to the internet must be authorized on UTM. Such devices can be called static and authorization by MAC address is perfect for them.
In order to authorize a network printer, you need to create a user for this printer manually or through [**Netscan**](https://docs.safedns.com/books/42-setup-users/page/netscan). [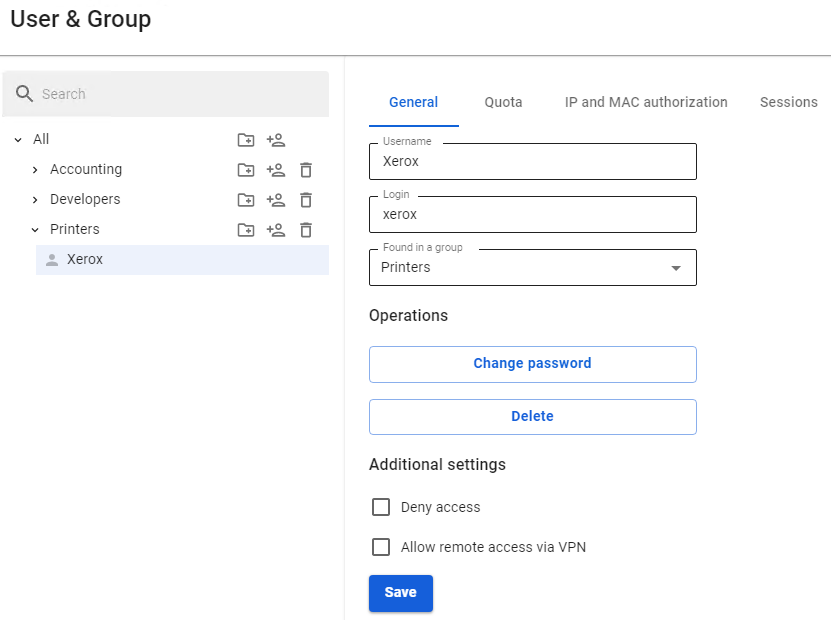](https://docs.safedns.com/uploads/images/gallery/2022-08/Vis8OH4FW5lCuz2W-7-authorization-by-mac-address.png) For a network printer, in **Users -> Authorization -> IP and MAC authorization you** need to create a rule **User <--> MAC address. [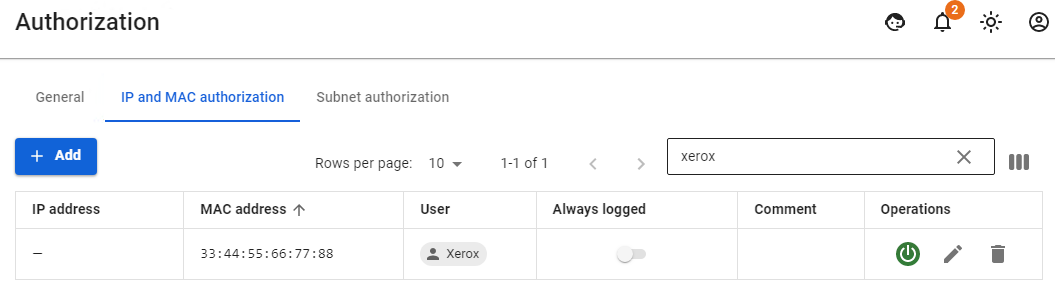](https://docs.safedns.com/uploads/images/gallery/2022-08/NWDlzJwih6eWEDLS-8-authorization-by-mac-address.png)** When detecting activity from a network printer or other device, its user will immediately appear in **Monitoring -> Authorized users.**In modern phones, there is an option for **MAC Randomization**. This option will interfere with phone authorization by MAC address. It is recommended to disable this option or use other types of authorization (for example, [**web authorization**](https://docs.safedns.com/books/42-setup-users/page/web-authorization))
# VPN Connections # VPN Connection To gain access from outside (from home, hotel, or another office) to the enterprise's local network located behind SafeUTM, you can connect via VPN from this machine (computer or mobile device) to the SafeUTM server. For client-to-site VPN, our server supports four tunneling protocols: [**IKEv2**](https://docs.safedns.com/books/42-setup-users/page/ipsec-ikev2), [**SSTP**](https://docs.safedns.com/books/42-setup-users/page/sstp), [**L2TP/IPsec**](https://docs.safedns.com/books/42-setup-users/page/l2tp-ipsec), and [**PPTP**](https://docs.safedns.com/books/42-setup-users/page/authorization-by-pptp).For security reasons, it is not recommended to use the PPTP protocol (it is left for compatibility with outdated operating systems and equipment, as well as for authorization in a local network where there are no requirements for strict traffic encryption).
**IKEv2 protocol is recommended in terms of speed and security.** You can use the [**user's personal account**](https://docs.safedns.com/books/42-setup-users/page/users-personal-account) to distribute instructions on creating custom VPN connections. # Authorization by PPTPDo not use this type of connection. This connection method is EXTREMELY insecure and has been left solely for compatibility with older solutions. Use **IPsec-IKEv2**.
Authorization by PPTP protocol involves authorization via a secure network tunnel between the user’s network device and the SafeUTM internet gateway. - A login/password bundle is used for user authorization and Active Directory users. - To authenticate by PPTP protocol you need to assign an IP address to a network device, as well as configure a connection using the PPTP protocol, specifying the SafeUTM gateway IP address as the PPTP server address. Upon successful authorization and establishment of a network tunnel, an additional IP address will automatically be assigned to the network device to gain access to internet resources. Using authorization by PPTP does not affect the ability of a network device to access LAN resources in any way. --- #### Configuring SafeUTM Global Settings To set up authorization by PPTP protocol you need to perform the following actions: 1. Go to **Users -> VPN connections**. 2. Select **PPTP Authorization** and click **Save**. [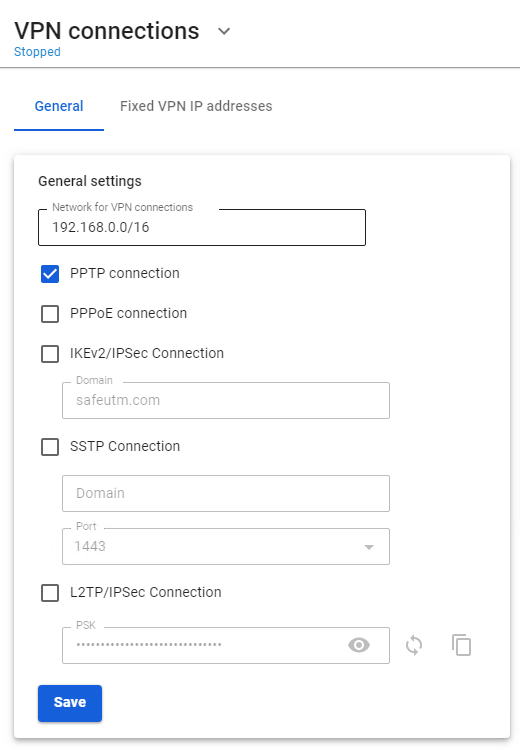](https://docs.safedns.com/uploads/images/gallery/2022-08/d6B9TQesKTZXjMTq-1-authorization-by-pptp.png) You can edit your login and password in the tab **Users -> User & Group** upon selection of a necessary user. [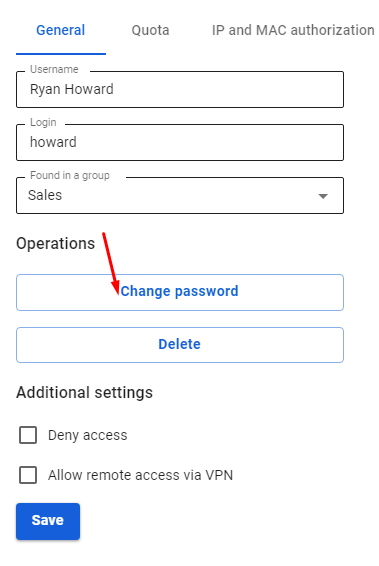](https://docs.safedns.com/uploads/images/gallery/2022-08/mOvMe1PVo2m7JWQS-2-authorization-by-pptp.png) The user is assigned an IP address automatically from the pool of addresses for VPN configured in the section **Users -> VPN connections** (for example, 10.128.0.0/16). In order to set up a **static** binding of addresses issued via VPN to certain users, go to **Users -> VPN connections -> Fixed VPN IP Addresses**, click "+ Add" and specify the intended user and IP address. An example of a fixed VPN IP address can be seen below: [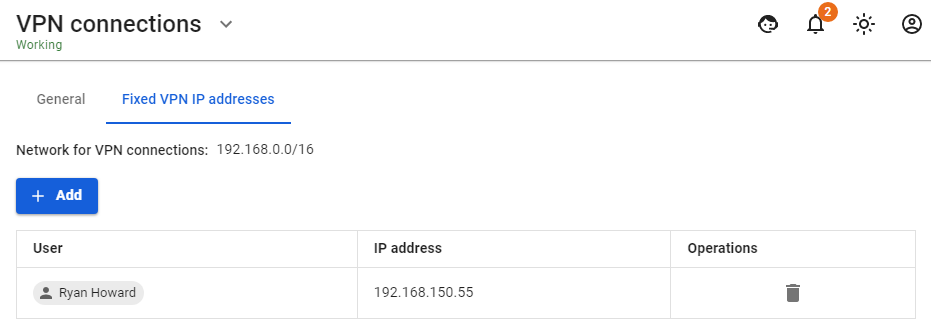](https://docs.safedns.com/uploads/images/gallery/2022-08/3rJ9igeJzXSwTiOD-3-authorization-by-pptp.png)When connecting from the internet, we recommend using IPSec IKEv2, L2TP IPSec, or SSTP for more reliable traffic encryption. --- #### Configuring Users in SafeUTM Allow the user to connect via VPN from the Internet by checking in the user settings (**Users -> User & Group -> General tab**) in the box **Allow remote access via VPN**. --- #### Possible Problems - The provider from the gateway’s side or from the connected client’s side blocks the GRE protocol with which the PPTP connection takes place. In this case, when trying to connect to an external SafeUTM address, error 619 will occur. You can determine on which side the problem is by connecting from different places and from different providers. If it is possible to connect from some places, it means that the problem is on the side of those clients who cannot connect. When the provider is determined, you need to try to solve the problem with them or use [**IPsec-IKEv2**](https://docs.safedns.com/books/42-setup-users/page/ipsec-ikev2) or [**SSTP**](https://docs.safedns.com/books/42-setup-users/page/sstp). - TCP port 1723 is blocked. You can check the port availability using standard network utilities such as telnet. If there is no connection to this port, then the tunnel cannot be established. - The user's username or password is incorrect. If this happens, it is often suggested to specify the domain when reconnecting. Try to create alphanumeric passwords, preferably in Latin, for your accounts. If the password is entered incorrectly more than 6 times, the user's IP address will be blocked by the password attack protection service. - If the connection is made with Windows OS, then in order for the packets to go through it, you need to make sure that the following box is checked in the connection settings **Use default gateway on the remote network** in the section **VPN connection properties -> Network tab -> Internet Protocol Version 4 (TCP/IPv4) properties -> Advanced**. If it is not necessary to route all packets to this interface, then the route must be written manually. - When the error **The connection was terminated by the remote computer** occurs, it is necessary to enable MPPE 128-bit support (In Windows this option is enabled by default) and only check MSCHAPV2 among authorization protocols. --- #### If a VPN connection is established but it is not possible to access local network resourcesAuthorization by PPPoE is possible only in one Ethernet segment with local SafeUTM interfaces.
# IPSec IKEv2This VPN protocol is preferable and recommended for all usage scenarios. Instructions for setting up VPN connections on different operating systems are available [**here**](https://docs.safedns.com/books/6-instructions-and-troubleshooting/chapter/instructions-for-creating-vpn-connections).
--- #### Setting up VPN Server in SafeUTM 1. To enable authorization by IKEv2, check the corresponding box **Connection via IKEv2/IPsec** in the Web interface section **Users -> VPN connections**. 2. Routes are transmitted to clients to your local networks automatically. To control access to networks, use [**Firewall**](https://docs.safedns.com/books/44-setup-traffic-rules/page/firewall). 3. Connection is possible only by domain name (not by IP address), therefore it is necessary to have a domain name that resolves to the IP address of the SafeUTM external interface. In the **Domain** field, this DNS name must be specified. It is necessary to issue a Let's Encrypt certificate. [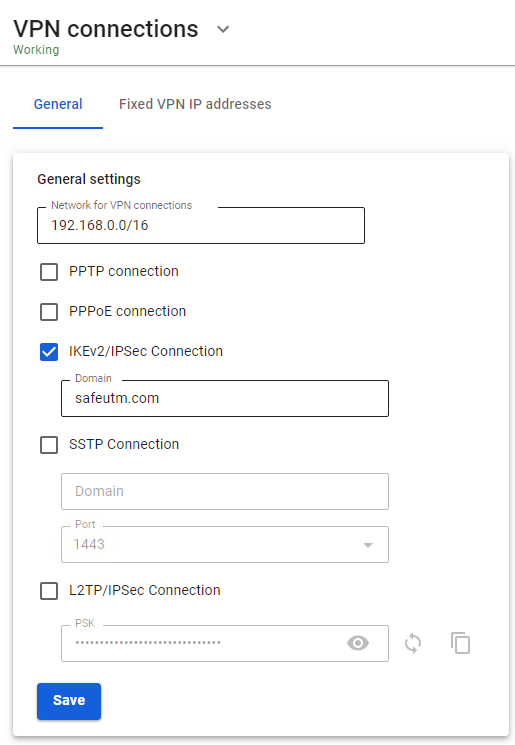](https://docs.safedns.com/uploads/images/gallery/2022-08/qCSx7gV5jXh1VO4M-1-ipsec-ikev2.png) 4. For users who need to connect from outside via VPN, check the box **Allow remote access via VPN** in the user tree. The username and password specified here will be used to connect. --- #### IPsec IKEv2 Support in Client OS - Microsoft **Windows 7** (2009). Requires installation of a Let's Encrypt root certificate - Apple **MacOS X 10.11** "El Capitan" (2015) - Linux [**NetworkManager plugin**](https://wiki.strongswan.org/projects/strongswan/wiki/NetworkManager) (since 2008) - Google **Android 11** (2020). On older versions, you can use the [**StrongSwan**](https://play.google.com/store/apps/details?id=org.strongswan.android) application - Apple **iOS 9** (iPhone 4S) (2015) - **KeeneticOS 3.5** - Mikrotik - Cisco routers # SSTP SSTP (Secure Socket Tunneling Protocol) is a protocol of secure traffic tunneling based on SSL/TLS. It is supported by Windows OS Vista and above, as well as Mikrotik, Keenetic routers, and others. ---If possible, do not use this type of connection. This connection method passes through NAT better than others, but with unstable communication quality, it works much worse than other VPNs (especially when transmitting audio/video), since it encapsulates all data inside TCP. It is recommended to use IPsec-IKEv2 instead of SSTP. UTM does not support Mikrotik connection over SSTP because Mikrotik uses an old and insecure SHA-1 algorithm.
--- #### Setting up SafeUTMIt is not recommended to use SSTP for VPN connections from the local network.
1\. To enable SSTP, check the box **SSTP connection in the web interface in **Users -> VPN connections**. 2\. Connection is possible only by DNS name, so the IP address of SafeUTM external interface should resolve to one of the names of your external domain zone. In the **Domain** field, you need to specify this DNS name (use the real name with the correct A-record, because it is necessary for issuing a Let's Encrypt certificate). 3\. **Port** - select the suggested port (from the options: 1443, 2443, 3443, 4443). [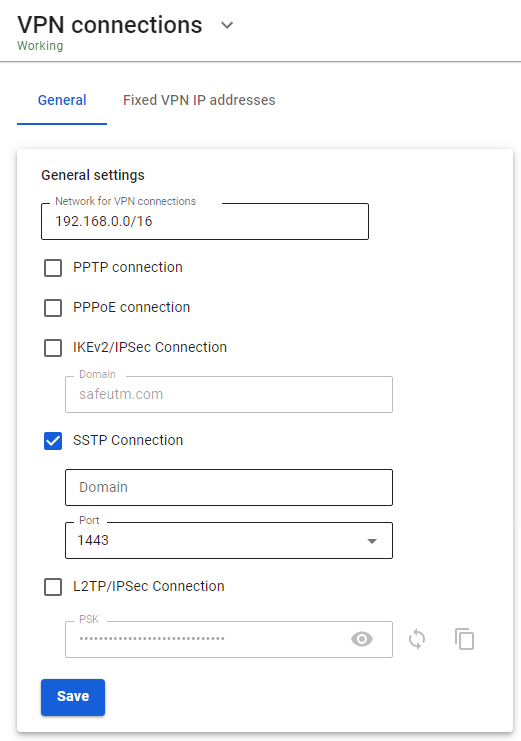](https://docs.safedns.com/uploads/images/gallery/2022-08/wWO8efWPVrKELnzv-1-sstp.png)4. For users who need to connect from outside via VPN, check the box **Allow remote access via VPN** in the user tree. The specified username and password will be used for the connection.VPN setup instructions for different operating systems can be found [**here**](https://docs.safedns.com/books/6-instructions-and-troubleshooting/chapter/instructions-for-creating-vpn-connections).
--- #### If a VPN connection is established but it is not possible to access local network resourcesIf possible, do not use this type of connection. This connection method can be unstable, has huge redundancy, has low performance, and does not support the strongest encryption. IPsec-IKEv2 is recommended instead. All modern operating systems support IKEv2, or there are applications for them.
--- #### Configuring SafeUTM Global Settings 1\. Go to **Users -> VPN connections.** 2\. Check the box **L2TP/IPsec Connection.** 3\. Enter the secret phrase (PSK key). 4\. Click on **Save**. [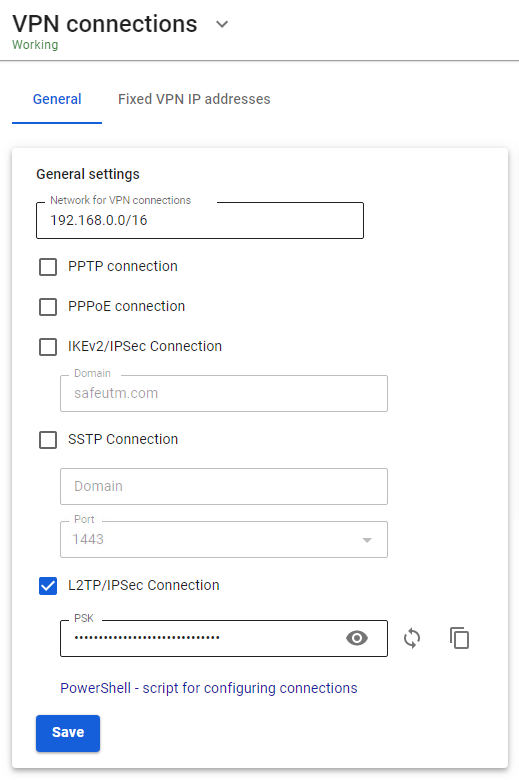](https://docs.safedns.com/uploads/images/gallery/2022-08/0zN8AYv3Pw5d3rl0-1-l2tp-ipsec.png) --- #### Configuring Users in SafeUTM Allow the user to connect via VPN from the Internet by checking in the user settings (**Users -> User & Group -> General tab**) in the box **Allow remote access via VPN**.L2TP IPsec clients behind the same NAT may experience connectivity issues if there is more than one client. [**Instructions**](https://docs.microsoft.com/en-us/troubleshoot/windows-server/networking/configure-l2tp-ipsec-server-behind-nat-t-device) can help solve the problem. We recommend using [**IKEv2 IPSec**](https://docs.safedns.com/books/42-setup-users/page/ipsec-ikev2) instead of L2TP IPsec.
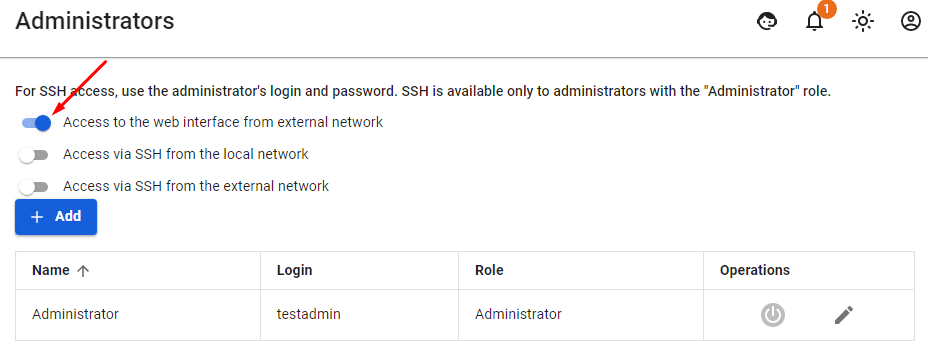
--- #### If a VPN connection is established, but you cannot access local network resources Follow the recommendations in the article [**Features of Routing and Access Organization**](https://docs.safedns.com/books/42-setup-users/page/features-of-routing-and-access-organization). # User's Personal Account --- To quickly configure user connections, you can enable access to the SafeUTM web interface. In the personal account accessible with the use of SafeUTM accounts details (local or domain, in case of [**integration with Active Directory**](https://docs.safedns.com/books/42-setup-users/page/integration-with-active-directory)), users will be able to download ready-made PowerShell scripts to create user connections and a link to instructions for setting up a VPN and running scripts. You can enable access from the Internet to your personal account and SafeUTM administration web interface in the section **Server Management -> Administrators** by enabling the setting **Access to the web interface from external network**. After enabling the parameter, the personal account and the web administration interface will be accessible by the IP address of the SafeUTM external interface.If the external IP address of SafeUTM is not included in the "white" networks, then you need to forward port 8443 on the upstream device.
[](https://docs.safedns.com/uploads/images/gallery/2022-08/V7uX0BuD6mqVbqwO-1-users-personal-account.png) When logging in under a user account (including those imported from Active Directory), it will be possible to download scripts for creating VPN connections and a link to instructions for their implementation. Users will also be able to remotely administer the SafeUTM server. # Features of Routing and Access Organization --- #### If VPN is required only to access local network resources If you need to access the Internet directly through your provider, and you need to use a VPN only to access corporate network resources on computers connected via VPN, you need to configure the following settings. - In the VPN connection properties, uncheck the box **Use primary gateway on remote network**. Tab **Network -> Internet Protocol version 4 -> Advanced -> IP Settings**. [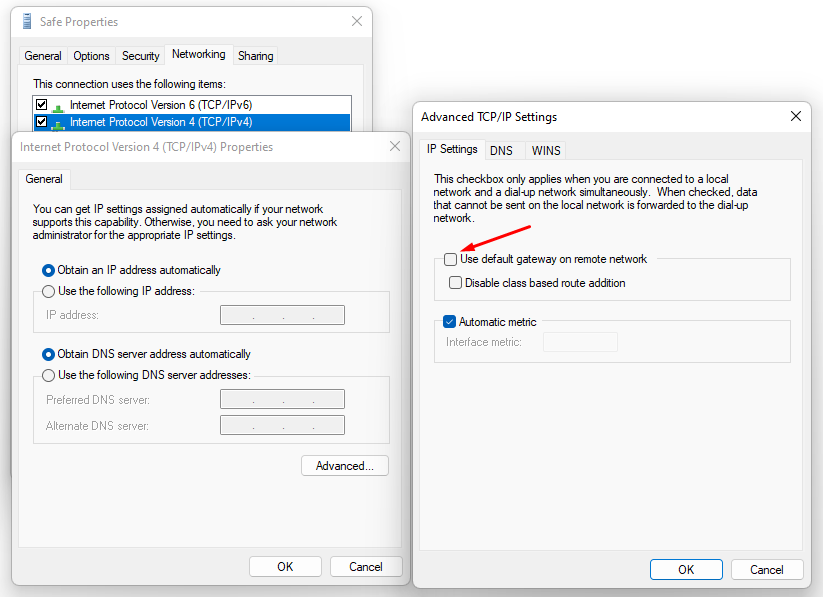](https://docs.safedns.com/uploads/images/gallery/2022-08/c4KDykIAEjVxa3iy-1-features-of-routing-and-access-organization.png) - Create a route to the corporate network (**in Windows 7, 8, 8.1, and 10, a route based on the class will be automatically created, depending on the address that the connection will receive via VPN. For example, a route will be added for the 10.0.0.0/8 network if the VPN server receives an address from the 10.128.0.0/16 network**). For IPsec-IKEv2, you can configure automatic route acquisition. Route example: if the corporate network is `172.16.0.0/16`, and the network for VPN connections is configured to SafeUTM `10.128.0.0/16` (and the IP address is issued to the VPN connection from the same network), then the route will be: `route -p add 172.16.0.0 mask 255.255.0.0 10.128.0.1` - In some cases, the route may not work, then there is a ping to the protected interface (`10.128.0.1`), but there is no ping to the hosts in the LAN. In this case, when creating a route, you need to specify the number of the VPN connection interface. The final route will be as follows: `route -p add 172.16.0.0 mask 255.255.0.0 10.128.0.1 if nn`where **nn** is the number of the VPN connection interface which can be viewed when the VPN connection is active in the output of the route print command in the console section **List of Interfaces**. --- #### If it is not possible to access computers in the local SafeUTM network - Make sure that the local network (or the address on the network card) on the remote machine does not intersect with your organization's LAN, if it intersects, then there will be no access to your organization's network (traffic on the routing table will go to the physical interface, and not to VPN). **Addressing must be changed.** - SafeUTM must be registered as the main gateway on LAN computers. If this is not the case, then you need to register the appropriate route manually on the devices, so that network packets go to SafeUTM for the VPN network. **Example:** `route -p add 10.128.0.0 mask 255.255.0.0 10.1.1.1`where `10.128.0.0/16` is the address of the SafeUTM VPN network (configured in **Users -> VPN connections**), and `10.1.1.1` is the IP address of the local SafeUTM interface. - Check the firewall settings (**FORWARD table**) in SafeUTM for prohibiting rules. - Computers and servers on Windows OS can restrict access to network folders using network profile settings rules (both on the side of the computer connecting via VPN, and on the side of computers and servers in LAN): [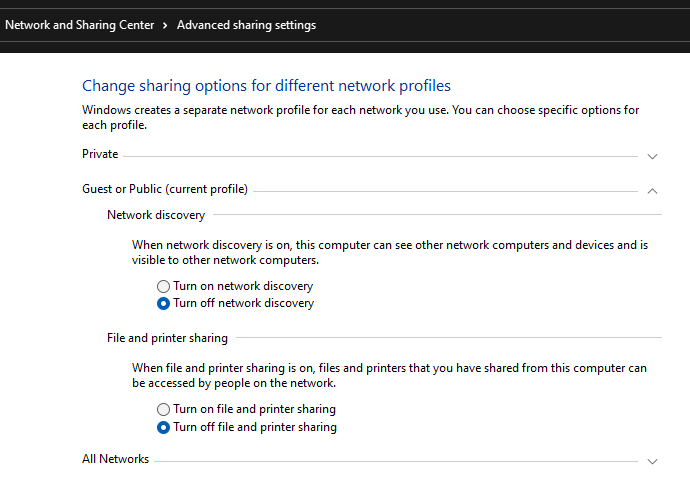](https://docs.safedns.com/uploads/images/gallery/2022-08/ua0fKDtvxrqtnLw5-2-features-of-routing-and-access-organization.png) **Enable access to files and printers for All Networks and Private Networks profile.** You can do this using PowerShell (launched with rights elevated to the administrator) by running the command:`Enable-NetFirewallRule -Group "@FirewallAPI.dll,-28502"` - Windows Defender Firewall may block access to certain programs or services (including RDP) to external networks. Check it in the settings of incoming and outgoing connections (you need to allow access from frequent and local networks): [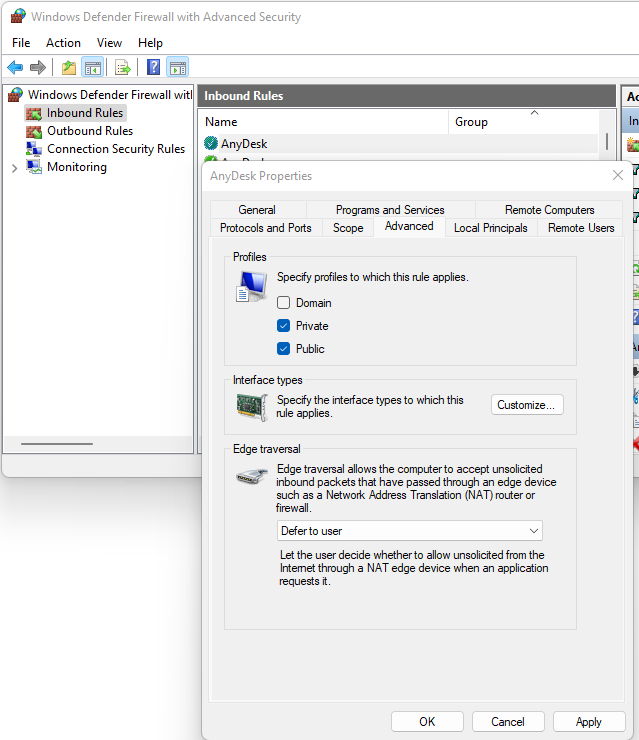](https://docs.safedns.com/uploads/images/gallery/2022-08/piWnhIA8wFzQLuGP-3-features-of-routing-and-access-organization.png) - Antivirus software on the computer may block access to it from non-local networks. Or block access to specific programs. For example, for some antiviruses, it is necessary to add a network for VPN connections (10.128.0.0/16 by default ) to exceptions. # Instructions for running PowerShell scripts Use ready-made scripts downloaded from your server to create a VPN connection in Windows versions 8.1 and 10. --- If you are using Windows 7, you must create the connection manually (see [**Manually create user-side VPN connections**](https://docs.safedns.com/books/6-instructions-and-troubleshooting/page/creating-a-vpn-connection-in-windows-7)). --- #### Which VPN protocol should I choose? With several options for possible VPN connections, choose protocols according to the following criteria: 1. **IKEv2/IPsec** is the best protocol in terms of performance and connection reliability. 2. **SSTP** is a protocol based on TCP and SSL. Choose it if the IKEv2 connection does not go through your provider. 3. **L2TP/IPsec** is reliable in terms of encryption, but not the most optimal in terms of speed and performance. --- #### How do I run a PowerShell script? 1\. Download the script: **From SafeUTM:** - By navigating to the section **Users -> VPN connections** - Set the flag for the required connection protocol, if required, fill in the fields and click **Save** - Click on the link ****PowerShell - script to configure connections****[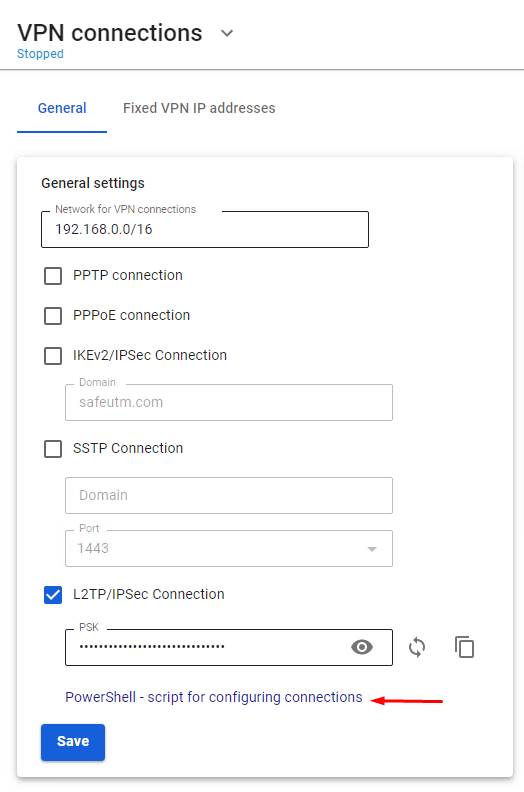](https://docs.safedns.com/uploads/images/gallery/2022-08/qfmLoiRQEcP69ATT-1-instructions-for-running-powershell-scripts.png) - Transfer the downloaded file to the device where you want to create a VPN connection. 2\. Right-click on the downloaded file and select **Properties** from the context menu. [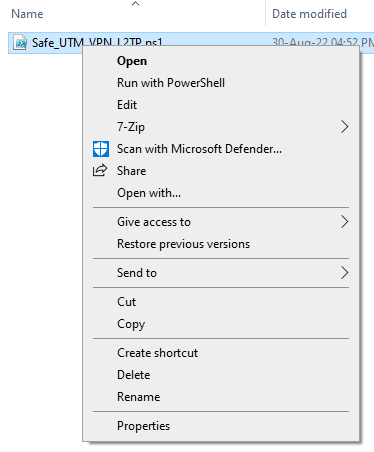](https://docs.safedns.com/uploads/images/gallery/2022-08/xAXZg1MYLVsLVTY3-2-instructions-for-running-powershell-scripts.png) 3\. Check the box **Unlock** in the lower right corner of file properties (by default, the OS blocks the execution of files downloaded from the Internet) [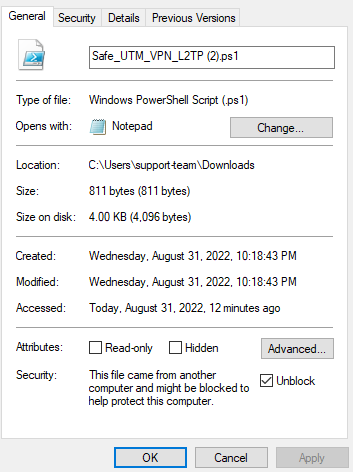](https://docs.safedns.com/uploads/images/gallery/2022-08/KSQl8KupCppF7VX7-3-instructions-for-running-powershell-scripts.png) 4\. Right-click on the file again and select **Run in PowerShell** in the context menu. [](https://docs.safedns.com/uploads/images/gallery/2022-08/4HkybbL3wfpmXMbK-4-instructions-for-running-powershell-scripts.png) If the error "Script execution is disabled on this system" appears, you need to enable script execution by running the command in PowerShell (call it up from the Start menu): `Set-ExecutionPolicy Unrestricted` 5\. Answer **Yes** to the question about making changes to your computer. 6\. The connection is created. Click **Connect** in the list of your networks. --- #### What should I do if I can't run the script? You may not have enough rights to run scripts or PowerShell is not installed on the system. Use the instructions for creating a connection in [**Windows 10**](https://docs.safedns.com/books/6-instructions-and-troubleshooting/page/creating-a-vpn-connection-in-windows-10) and [**Windows 7**](https://docs.safedns.com/books/6-instructions-and-troubleshooting/page/creating-a-vpn-connection-in-windows-7). # Subnet Authorization This type of authorization allows you to create an authorization rule for a specific UTM user from a specific subnet --- In order not to register each device as a separate UTM user and not to fix authorization factors for it, you can use Subnet Authorization. This feature will allow a UTM user from the desired subnet to auto-authorize without being tied to a MAC and/or specific IP and will be useful if a large number of devices need to be auto-authorized.Traffic across the entire subnet will be recorded per user. In a network for which a Subnet Authorization rule has been created, DHCP can work.
For example, there is a WiFi subnet on the 192.168.10.0/24 subnet from which devices should be allowed to log in. Create an authorization rule: 1\. Go to the **Users –> User & Group** section and click Add user 2\. Fill in the fields Subnet name, Login, and click Save[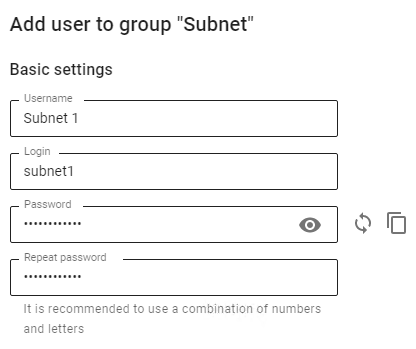](https://docs.safedns.com/uploads/images/gallery/2022-08/hmOElVLDg8T6u5XY-1-subnet-authorization.png) 3\. Go to the section **Users –> Authorization –> Subnet authorization** and click **Add** in the upper left corner 4\. Fill in the fields and click **Save**: - User - select the user created in step 2 - Subnet - enter IP and subnet mask - Comment - (optional) [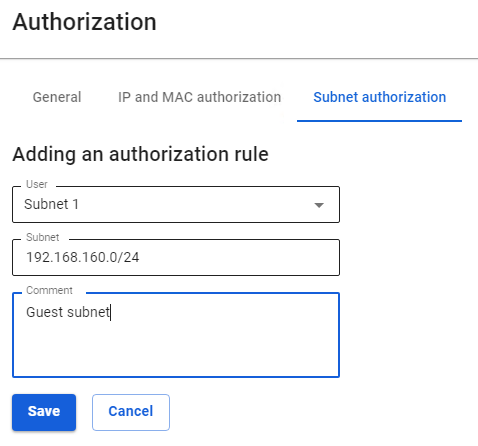](https://docs.safedns.com/uploads/images/gallery/2022-08/5zgWtgyh9uPK6xnd-2-subnet-authorization.png)**Be careful when creating Subnet authorization rules** There will be problems with authorization if: - There are overlapping networks for different users - There are rules for authorizing users by IP addresses from a subnet in the Subnet authorization rule; - Rules have been created in the **Fixed VPN IP addresses** subsection with binding to an IP address from the subnet of the Subnet authorization rule.
# Fixed VPN IPs The section allows you to bind a specific IP address for a specific user for VPN connections. ---If you create a fixed binding for any user, then only one active VPN session will be possible for this user.
For example, you have a host on a local network that only users with certain IP addresses can connect to. To provide direct VPN access to this host, go to **Users -> VPN connections -> Fixed VPN IP addresses**, click **Add**, fill in the **User** and **IP address** fields, and click **Apply**. [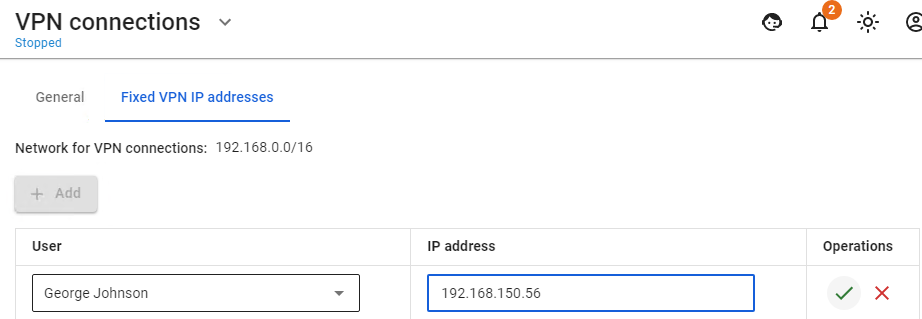](https://docs.safedns.com/uploads/images/gallery/2022-08/HoF3HnL25JRx43El-1-fixed-vpn-ips.png) # Integration with Active Directory # Integration with Active Directory SafeUTM provides the possibility of one-way synchronization with a domain based on Microsoft Active Directory. --- Only accounts are imported, excluding passwords. When the user undergoes the authorization procedure, verification is carried out by means of Active Directory.Integration with Windows Server 2008 (only R2), 2012, 2016, and 2019 is supported.
--- #### Features of Using Integration with Multiple Active Directory Domains When integrating SafeUTM with multiple domains, the following limitations apply: - From the Active Directory domain tree, only the data of the domain controller to which SafeUTM is connected is imported into SafeUTM. - With Single Sign-On authorization, when the browser is opened for the first time, the user will be offered a choice of domains for authorization. The selection will be saved using a cookie and will be used at the next authorization. If you want to change the domain, delete the cookie (for the local SafeUTM IP address). --- #### Using Security Groups and Accounts Imported from LDAP as Filter Rule Objects Security groups and accounts imported from Active Directory can be used as filter rule objects in the following sections: - [**Firewall**](https://docs.safedns.com/books/44-setup-traffic-rules/page/firewall) - [**Application control**](https://docs.safedns.com/books/44-setup-traffic-rules/page/application-control) - [**Traffic Shaping**](https://docs.safedns.com/books/44-setup-traffic-rules/page/traffic-shaping) - [**Content Filter**](https://docs.safedns.com/books/44-setup-traffic-rules/page/content-filter) Usage example: 1. Import accounts and/or security groups from Active Directory in the **Users -> User & Group** section (for more details, see [**Import of Users**](https://docs.safedns.com/books/42-setup-users/page/import-of-users)). This example imports the AD security group ****Domain Users:****[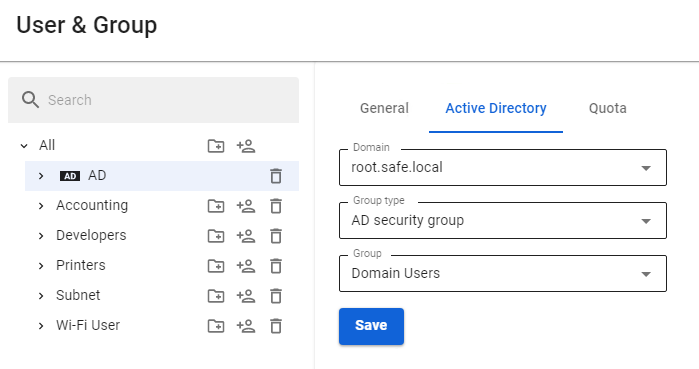](https://docs.safedns.com/uploads/images/gallery/2022-09/bg5N1FJhmW9rRnka-1-integration-with-active-directory.png) 2. Go to the section where you want to use a group or account imported from Active Directory. For example, in Application Control: [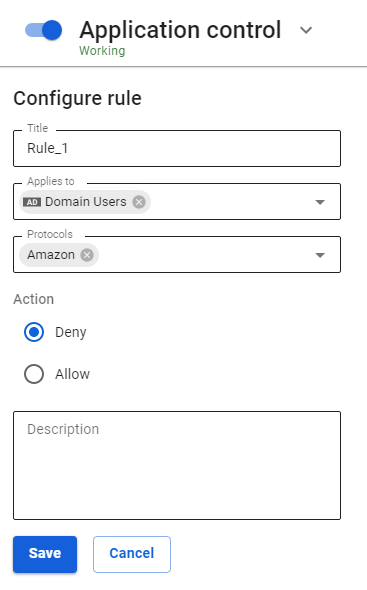](https://docs.safedns.com/uploads/images/gallery/2022-09/XPhrBS22ey9Hud8K-2-integration-with-active-directory.png) 3. Fill in the required fields and click **Save**. # Active Directory User Authorization ---Import accounts from Active Directory, see [**Import of Users**](https://docs.safedns.com/books/42-setup-users/page/import-of-users) for details.
--- #### Setting up user authorization For users imported from Active Directory, all types of user authorization are available. The most commonly used user authorization options are Single Sign-On authentication via Active Directory using Kerberos/NTLM for authorization via a web browser and authorization via the Active Directory security log (simultaneous use of both types of authorization is recommended). --- #### Setting up SafeUTM To enable **Single** **Sign-On Authentication** and **Authorization through the Active Directory Security Log**, go to the **Users -> Authorization -> General** tab and enable these authorization types. Next, click the **Save** button. [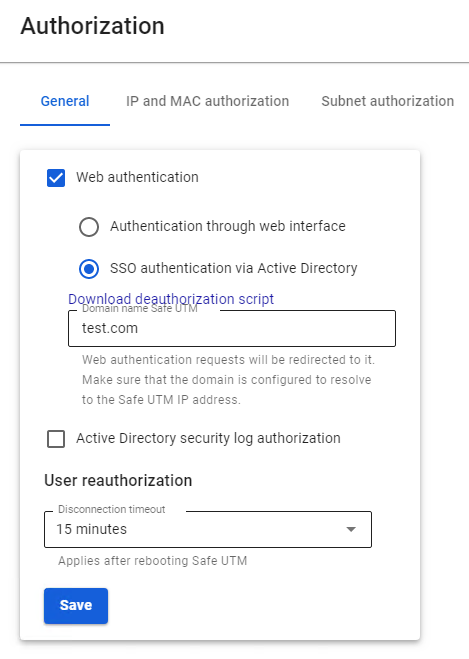](https://docs.safedns.com/uploads/images/gallery/2022-09/hh8H3p9NpvZHb77J-1-active-directory-user-authorization.png)After filling in the Domain name field and saving the settings, a Let’s Encrypt certificate will be issued and the user will be redirected to the authorization window, bypassing the security exception page. If a certificate for such a domain has already been loaded in the [**TLS Certificates**](https://docs.safedns.com/books/45-setup-services/page/tls-certificates) section, then it will be used and a new certificate will not be issued.
--- #### Configuring user computers and domain policies ##### Authorization via Active Directory security logSupported starting with the 2008 standard edition domain controller.
For authorization through the security log to work, you must configure the following settings on the primary domain controller: - In the Windows firewall settings on all domain controllers (or domains), allow Remote Event Log Management (RPC) [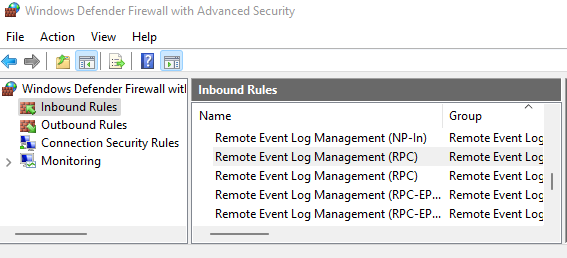](https://docs.safedns.com/uploads/images/gallery/2022-09/sps6cwKMhfefYvAl-2-active-directory-user-authorization.png) - Add SafeUTM to the Event Log Readers security group. - After configuring access to the log, it is necessary to restart the **Active Directory security log authorization** service on SafeUTM, to do this, disable this setting and re-enable it. - If you changed the security policies of domain controllers compared to the standard ones, then you need to enable logging-in security policies by activating the following setting: **Default Domain Controllers Policy -> Computer Configuration->Policies->Windows Settings->Security Settings-> Advanced Audit Policy Configuration - > Audit Policies -> Logon/Logoff -> Audit Logon -> Success**. - The following settings must also be enabled: **Default Domain Controllers Policy -> Computer Configuration->Policies->Windows Settings->Security Settings-> Advanced Audit Policy Configuration -> Audit Policies -> Account logon -> "Audit Kerberos Authentication Service" and "Audit Kerberos Service Ticket Operations" -> Success.** - To update domain controller policies, run the `gpupdate /force command` - If user authorization does not occur during login, you need to check the security log for events 4768, 4769, and 4624. --- ##### Web Authorization (SSO or NTLM) For authorization to work through a web browser (using Kerberos or NTLM), you need to configure Internet Explorer (other browsers pick up its settings). Be sure to use these settings, even if users usually log in through the security log, in some cases they will need to log in through the browser. In order to configure authorization through a web browser, you must perform the following steps: 1. Go to your browser's properties and go to the **Security** tab. 2. Select **Local Intranet -> Sites -> Advanced**. 3. In the window that opens, add a link to SafeUTM under the name under which you entered it into the domain. You need to specify two URLs: with `http://` and with `https://` In the screenshot below, SafeUTM is entered into the `example.com` domain under the name `safeics`. [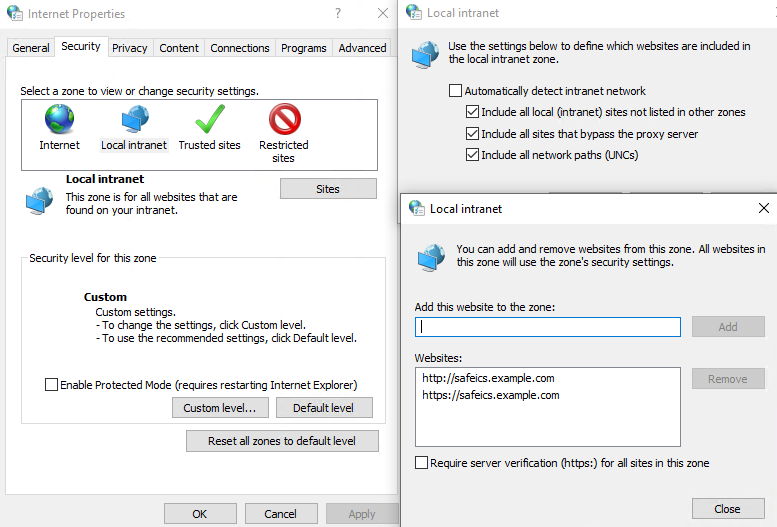](https://docs.safedns.com/uploads/images/gallery/2022-09/1W7p4NWNHm0zp2Nm-4-active-directory-user-authorization.png) Also, this setting can be made using Active Directory group policies for all users at once. To do this, you must perform the following steps: 1. In group policies for users, go to: **Default Policy Group > Computer Configuration > Policies > Administrative Templates > Windows Components > Internet Explorer > Internet Control Panel > Security Page > Site to Zone Assignment List** 2. Enter the zone assignment for the SafeUTM DNS name (safeics.example.com in the example) with a value of 1 (intranet). It is necessary to specify two destinations, for schemes of work on HTTP and HTTPS. [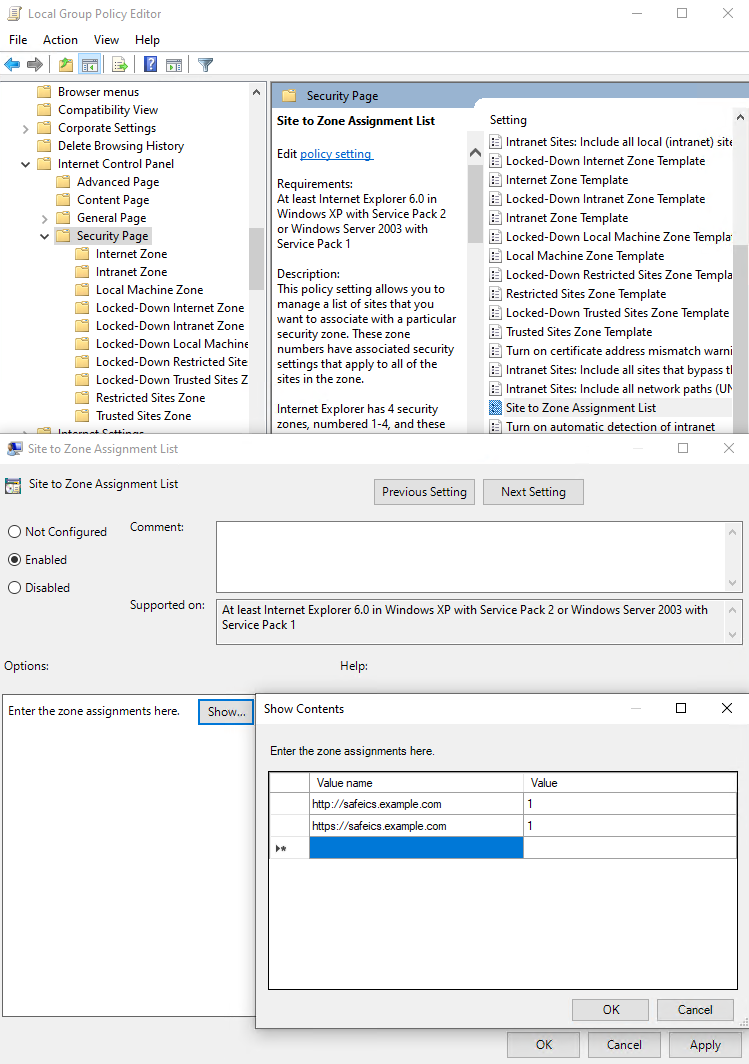](https://docs.safedns.com/uploads/images/gallery/2022-09/9mwDYXNUrD6u3Al5-5-active-directory-user-authorization.png)When entering an HTTPS site, for authorization, you must allow the browser to trust the SafeUTM certificate (in order not to do this every time, you can add the SafeUTM root certificate to the trusted root certificates of the device. For example, using domain policies). You can also use [**scripts to automatically authorize**](https://docs.safedns.com/books/42-setup-users/page/automatic-authorization-and-de-authorization-scripts) users upon login.
On the **Mozilla Firefox** browser settings page (about:config in the address bar), configure the following settings: - **network.automatic-ntlm-auth.trusted-uris** and **network.negotiate-auth.trusted-uris** add the address of the local SafeUTM interface (for example, safeUTM.example.com). - **security.enterprise\_roots.enabled** set to true will allow Firefox to trust the system certificate and authorize users when going to HTTPS sites. Also, for users imported via AD, the following authorization methods are possible: - **Authorization by IP address** - suitable if users always work from fixed IP addresses. IP addresses on UTM must be manually assigned to each user. - **Authorization via PPTP** - if the network has increased requirements for the confidentiality of information transmitted between the gateway and user devices, or if Wi-Fi is weakly protected from traffic interception. --- #### Configuring user authorization for direct connections to a proxy server Setting up transparent user authorization for direct connections to a proxy server is similar to setting up transparent **Single Sign-On** authorization described above in the instructions. The only difference is that the proxy server address is **not the IP address of SafeUTM, but its DNS name.** --- ##### Configuring the Mozilla Firefox browser for authorization via NTLM when connecting directly to a proxy server For computers that are **not in the Active Directory domain**, if they need to be authorized under a domain user account, configure the following settings on the **Mozilla Firefox** browser settings page (about:config in the address bar): - **network.automatic-ntlm-auth.allow-proxies** = false; - **network.negotiate-auth.allow-proxies** = false.Do not disable these options for computers that are members of an Active Directory domain, as in this case, the outdated NTLM authorization method will be used.
--- #### Possible causes of authorization errors - If a window appears in Internet Explorer with the text **Authentication is required** to gain access, and authorization occurs only when manually following the authorization link, then for some reason the browser does not redirect to the authorization page (it may be limited by browser security settings). In this case, set **Active Scripting** in Internet Explorer to **Enabled**. [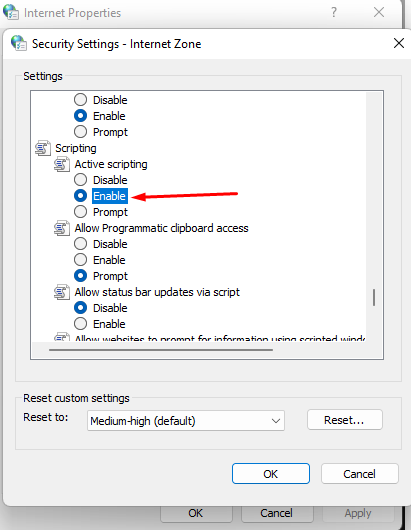](https://docs.safedns.com/uploads/images/gallery/2022-09/doiMdwf3YKXBfB6Q-7-active-directory-user-authorization.png) - The domain user must be allowed to log in to SafeUTM. On the domain controller, go to the properties of the selected users in the tab **Account -> Login to...**, select **only on specified computers** and enter the name of the workstation to log into the system. - With authorization through the security log of an Active Directory domain controller, users will be authorized when they try to access the Internet (any traffic). There is no automatic authorization without traffic passing through UTM because a competitive authorization policy is used. # Entering Server into Domain --- 1. Go to the tab **Users -> Active Directory**. 2. Click **Add**. 3. Fill in the following fields: - - **Domain**: enter the full domain name (domain DNS name, i.e., domain name, not domain controller). Maximum 64 characters. For example, `mydomain.example` - **AD DNS server**: enter the address of the server that has the role of a DNS server in Active Directory (as a rule, one of the domain controllers), accessible from the local SafeUTM interface. - **SafeUTM server name**: enter the server’s name. It can contain only letters (A-z), digits (0-9), and cannot begin or end with a hyphen. Maximum 15 characters. - **Login and password of a user with the right to join the domain**: this data is not stored on the server and is used once to join the domain. The user doesn’t have to be the domain admin, but they must have the right to join computers to the domain. An example of configuring integration with AD can be seen in the screenshot below: [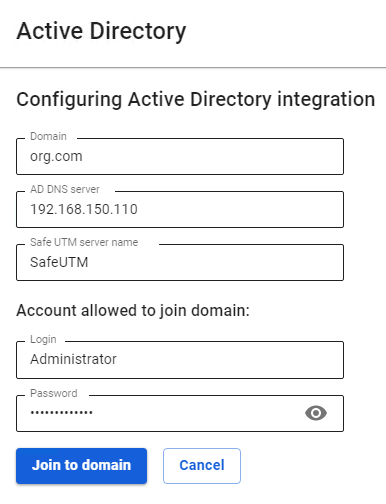](https://docs.safedns.com/uploads/images/gallery/2022-08/M0Ig2r8XO5BP3iAr-1-entering-server-into-domain.png)Attention: at least one domain controller must be located in the local SafeUTM network (or be accessible via a local interface using configured routing).
The process of joining the domain after clicking on the corresponding button may take up to one minute. It is possible to join the server to several Active Directory domains, with some features of work described in the article. --- #### Configuring DNS to Resolve Local Domain Names In the DNS server settings, in order for the synchronization of users and their authorization to work correctly, it is necessary to configure local domain name resolution on the server. To do so, in the DNS server settings you need to enter the Forward zone and DNS servers for it (as a rule, the main and backup domain controllers).In SafeUTM the DNS Forward zone is created automatically when the server is entered into the domain, and there is no need to configure it manually. Create it manually only if you mistakenly deleted this zone from the DNS server settings or if you failed to join the server to the domain.
[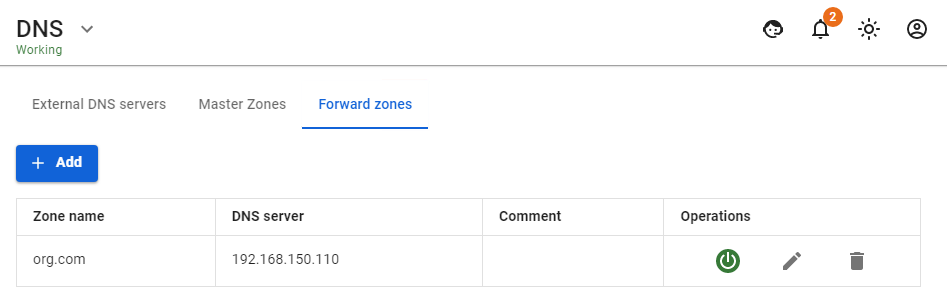](https://docs.safedns.com/uploads/images/gallery/2022-08/osA5NAEsp8lxkqAU-2-entering-server-into-domain.png) **In the example:** - **org.com** - Active Directory domain name. - **192.168.150.110** – domain controller IP address. With this setup, computers can use SafeUTM as the preferred DNS server. At the same time, the resolution of local and internet names will work correctly, also for all services provided by Active Directory. # Automatic Authorization and De-authorization Scripts Authorization and de-authorization of users are possible in fully automatic mode. For that, you need to configure scripts executed when users [**log on**](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc770908(v=ws.11)) and [**log out**](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc753583(v=ws.11)) of the system. For example, it can be done using domain group policies (GPOs).For these scripts to work, it is necessary to set up all domain and browser security policies described in [**User Authorization**](https://docs.safedns.com/books/42-setup-users/page/active-directory-user-authorization).
--- #### User Authorization You need to add the script to scenarios executed at the system [**log on**](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc770908(v=ws.11)). **UTMLogon\_script.vbs** ```VBScript Dim IE Set IE = CreateObject("InternetExplorer.Application") IE.Visible = True IE.Fullscreen = False IE.Toolbar = False IE.StatusBar = False Wscript.Sleep(3000) IE.Navigate2("http://google.com") Wscript.Sleep(20000) IE.Quit ``` --- #### User De-Authorization It is convenient to use this script when one computer is used by different users to go to internet resources. This script can be downloaded from the web interface by clicking **Download deauthorization script**. To do this, in the section **Users -> Authorization**, check the box **Web authentication**: [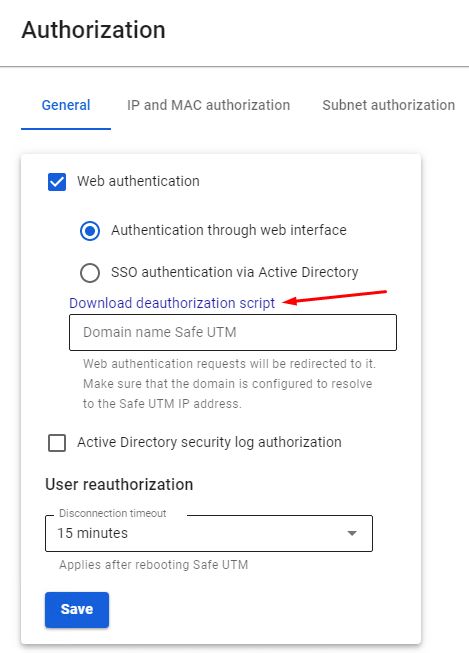](https://docs.safedns.com/uploads/images/gallery/2022-08/cp87ddx6RV0s4G5b-1-automatic-authorization-and-de-authorization-scripts.png) For user de-authorization to work, it is necessary to install the server certificate as a trusted root certification center on users’ computers. You can do this locally or through domain group policies, as described in the [**instructions**](https://docs.safedns.com/link/67#bkmrk-adding-certificate-v). You also need to disable the warning about certificate address mismatch in Internet Explorer properties: [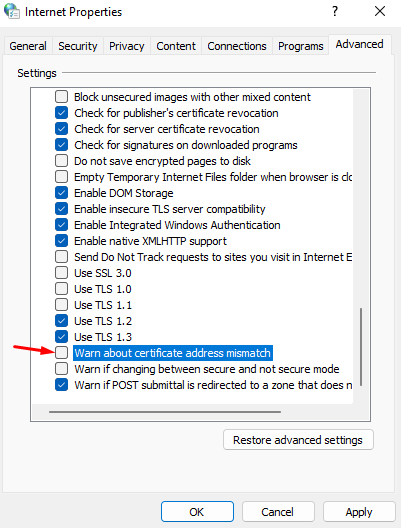](https://docs.safedns.com/uploads/images/gallery/2022-08/09gC6brhKGsjSXvY-2-automatic-authorization-and-de-authorization-scripts.png) This parameter can also be set up in GPO by changing the registry parameter: HKEY\_CURRENT\_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings parameter `WarnonBadCertRecving = 0` Next, you need to add the script executed when the user [**logs out**](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc753583(v=ws.11)) of the system: **UTMLogout\_script.ps1** ```Powershell add-type @" using System.Net; using System.Security.Cryptography.X509Certificates; public class TrustAllCertsPolicy : ICertificatePolicy { public bool CheckValidationResult( ServicePoint srvPoint, X509Certificate certificate, WebRequest request, int certificateProblem) { return true; } } "@ [System.Net.ServicePointManager]::CertificatePolicy = New-Object TrustAllCertsPolicy [Net.ServicePointManager]::SecurityProtocol = "tls12, tls11, tls" Invoke-RestMethod -Uri "https://In the future, users will be synchronized with Active Directory automatically every 15 minutes.
If necessary, you can use the query filter. For example, if you have users and computers in the same containers, and you want to import only users, write the following text in the **LDAP filter** field: `(&(objectCategory=person)(objectClass=user))` It is possible to import different AD user groups to different SafeUTM groups for the convenience of assigning firewall rules, content filtering, app control, bandwidth limitation, and other modules to them.You should not import subgroups of an already imported group, because they will automatically be imported together with the main group.
--- #### Importing Accounts from Security GroupsActive Directory users can only be imported into one SafeUTM group. Therefore, if it is in multiple Active Directory security groups, it will only appear in one of the UTM groups that were imported last.
You can import any number of AD security groups into different folders of the SafeUTM user tree. 1. Create a group in the SafeUTM user tree. 2. Select the group in the tree and go to the Active Directory tab. 3. Select the intended domain in **Domain Name**. 4. Select **AD Security Group** in **Group Type**. 5. In the field below select the intended security group from the drop-down list. 6. Click **Save**. An example of configuring the import of users from security groups can be seen in the screenshot below: [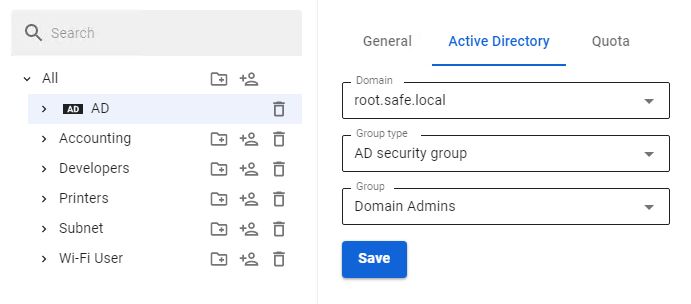](https://docs.safedns.com/uploads/images/gallery/2022-09/xyNXaGOFzWB1zUqA-2-import-of-users.png) # Netscan Automatic creation of a user with authorization by IP address for a device trying to access the internet via SafeUTM. ---**Netscan** creates MAC authorization for local addresses on a single Ethernet segment. If the device is located on a local network behind a router, then **Netscan** will create authorization by IP address. This module does not scan the network in search of devices but works in a passive mode.
A user will automatically be created when trying to access the internet in the specified group with the name corresponding to the IP address or NetBIOS name. If the NetBIOS name could not be determined, then by IP address. [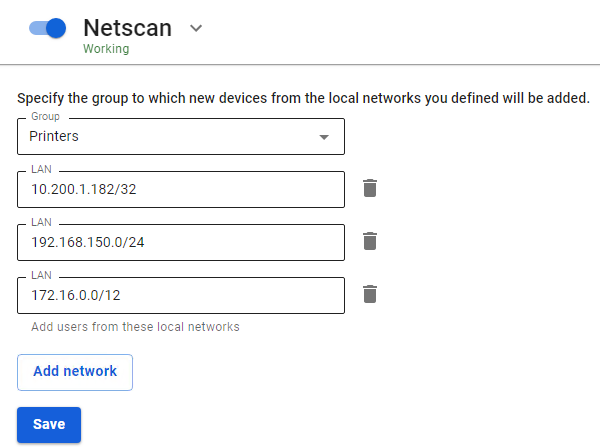](https://docs.safedns.com/uploads/images/gallery/2022-08/GygJOFCmZosgm8yi-1-device-detection.png) If necessary, you can restrict LANs, users from which will be automatically added and authenticated on SafeUTM. For example, this way you can authenticate users connecting via Wi-Fi or another open network.When connecting to UTM as a proxy server the Netscan system will not work.
# Wi-Fi Networks Configuring access point and router modes. --- In the current version, SafeUTM does not support Wi-Fi adapters. For wireless clients to work, it is necessary to use special wireless access points or Wi-Fi routers. To access the internet, users connected via Wi-Fi must be authenticated on UTM, or the Wi-Fi router needs to be authenticated. It depends on the operating mode of the device distributing Wi-Fi. ---