Application Control
The module implements in-depth traffic analysis (Deep Packet Inspection - DPI) to reveal protocols of popular apps (layer-7 filtering).
App control works only in the Enterprise edition for users with an active subscription to updates and technical support, as well as in the SafeDNS SMB edition with the purchased module. The list of compatible network adapters with which this model works for certain can be seen in the Installation Process section.
The Intrusion Prevention, Application Control, and Traffic Shaping rules do not handle traffic between LANs and branch networks.
See the Blocking Popular Resources article to find out how to block remote access software, anonymizers, torrents, and other popular resources.
The status of the module can be viewed by clicking on the checkmark icon at the top of the screen next to Application Control: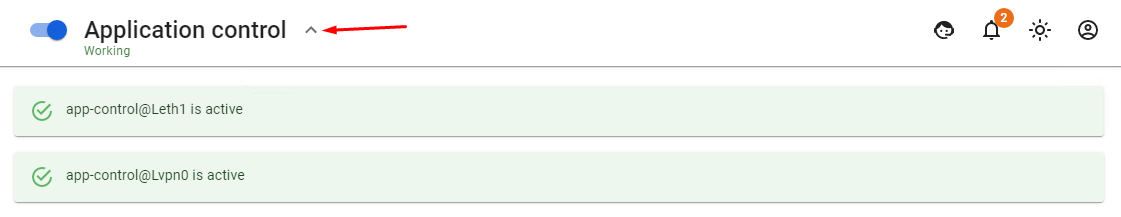
How the rule set works:
SafeUTM analyzes traffic and looks for a rule that matches this traffic from the list and applies it. If there are several rules in the list with the same conditions ("Applies to" and "Protocols" columns) but different actions (Action column), then the one with the higher priority will be applied.
Creating Rules
Rules are configured in Traffic Rules -> Application Control.
To create a new rule, follow these steps:
1. Click Add in the left upper corner of the screen.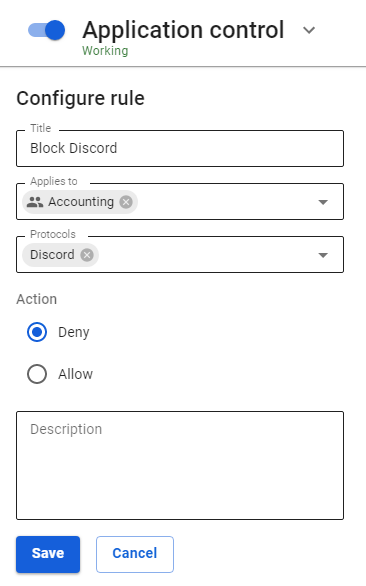
2. Specify the following parameters:
- Title – type in the rule name for the convenience of administration. Maximum 42 characters.
- Applies to – you can select objects of the following types: user, user group, IP address, IP address range, subnet, list of IP addresses, or a special object Quota Exceeded (users who exceed traffic quota fall in this object).
- Protocols – select (app) layer-7 protocol(s) from the list.
- Action – allow or deny the selected protocol.
3. Click Save.
