Connecting Devices
Description of options for connecting various routers (Mikrotik, Zyxel Keenetic, etc.) to SafeUTM for site-to-site VPN using IPsec IKEv2 protocol.
Devices that are not described in this manual as a rule can be connected using similar settings.
When combining networks using a VPN, LANs in different offices should not overlap.
The choice of crypto algorithms on remote devices.
When configuring third-party devices, you must explicitly specify the crypto algorithms used for the connection. SafeUTM supports the most up-to-date and at the same time sufficiently secure algorithms that do not load the server and devices. At the same time, outdated algorithms and those considered unsafe (MD5, SHA1, AES128, DES, 3DES, Blowfish, etc.) are not supported. When configuring third-party devices, as a rule, you can enter several supported algorithms at the same time. In fact, one algorithm of each kind is needed. Unfortunately, not all devices support the best algorithms, so SafeUTM supports several at once. Find below the list of algorithms of each type in descending order of priority for selection.
- Phase 1 (IKE):
- encryption:
- AES256-GCM
- AES256
- integrity (hash):
- for AES256-GCM - not required, since integrity check is built into AEAD algorithms.
- for AES256, by priority: SHA512, SHA256.
- prf (random value generation function):
- as a rule, it is configured automatically, depending on the choice of integrity algorithms (therefore, in the example below, the value of prf is PRF-HMAC-SHA512).
- for AES-GCM, you may need to specify explicitly. In this case, by priority: AESXCBC, SHA512, SHA384, SHA256.
- DH (Diffie-Hellman Group):
- Curve25519 (group 31)
- ECP256 (group 19)
- modp4096 (group 16)
- modp2048 (group 14)
- modp1024 (group 2)
- Timeouts:
- Lifetime: 14400 seconds
- DPD Timeout (for L2TP/IPsec): 40 seconds
- DPD Delay: 30 seconds
- encryption:
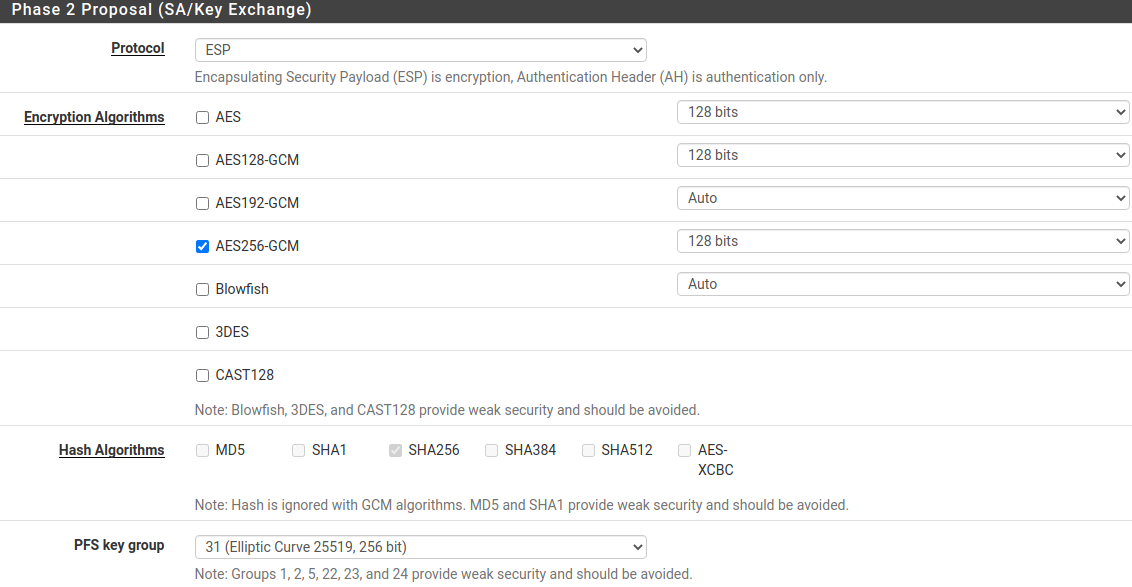
- Phase 2 (ESP):
- encryption:
- AES256-GCM
- AES256
- integrity:
- for AES256-GCM - not required, since integrity check is built into AEAD algorithms
- for AES-256, by priority: SHA512, SHA384, SHA256
- DH (Diffie-Hellman Group, PFS). ATTENTION! if not specified, it will connect, but rekey will not work after a while:
- Curve25519 (group 31)
- ECP256 (group 19)
- modp4096 (group 16)
- modp2048 (group 14)
- modp1024 (group 2)
- Timeouts:
- Lifetime: 3600 seconds
- encryption:
Example
- Phase 1 (IKE) (one of the lines is needed):
- AES256-GCM\PRF-HMAC-SHA512\Curve25519
- AES256\SHA512\PRF-HMAC-SHA512\ECP384
- AES256\SHA256\PRF-HMAC-SHA256\MODP2048
- Phase 2 (ESP) (one of the lines is needed):
- AES256-GCM\ECP384
- AES256\SHA256\MODP2048
An example of setting up a pfSense connection to SafeUTM via IPsec is shown in the screenshots below: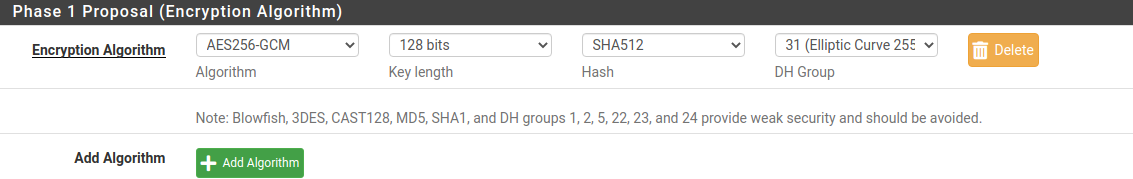
Connecting SafeUTM to MikroTik Using PSK
If there is a public IP address on the MikroTik device, follow the steps below to configure the SafeUTM connection to MikroTik.
Step 1.
Setting up SafeUTM
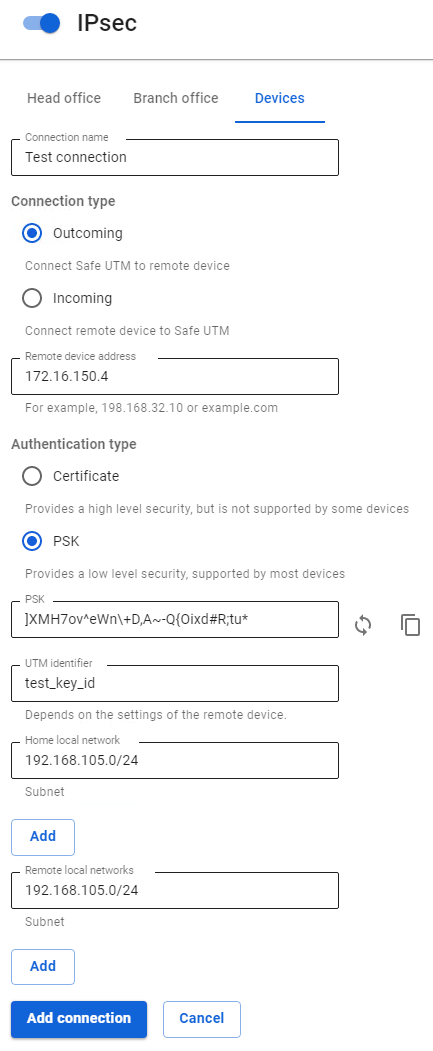
1. In SafeUTM, open the tab Services -> IPsec -> Devices, click on the icon (+), and fill in the following fields:
- Connection name – specify an arbitrary name for the connection. Maximum 42 characters.
- Connection type – select Outcoming, since the connection is made from UTM to MikroTik.
- Remote device address – specify the external IP address of the MikroTik device.
- Authentication type – select the PSK
- PSK – a random PSK key will be generated. You will need it to set up a connection in MikroTik.
- UTM identifier – the key you enter will be used to identify the outgoing connection.
- Home local network – list all UTM LANs that will be available in an IPsec connection, i.e. will be visible to the opposite side.
- Remote local networks – list all MikroTik LANs that will be available in an IPsec connection, i.e. will be visible to the opposite side.
2. After filling in all the fields, click Add connection. Your connection will appear in the list of connections: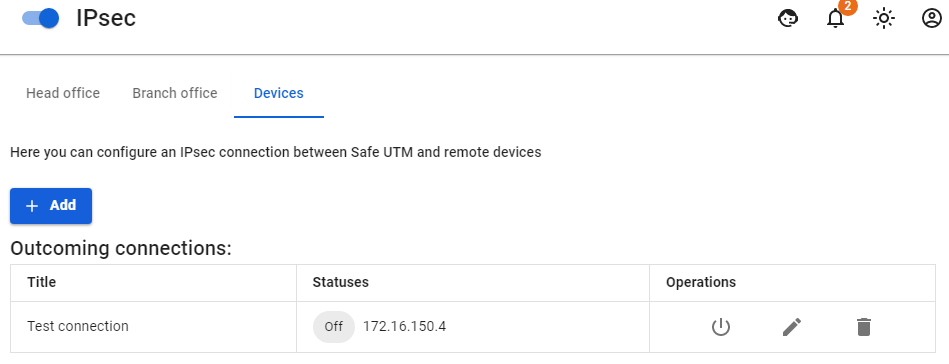
Step 2.
You can configure the MikroTik device in several ways - through the GUI, and through the device console.
Connecting MikroTik to SafeUTM Using PSK
If there is a public IP address on SafeUTM, follow the steps below to configure the connection of the MikroTik device to SafeUTM.
Step 1.
You can configure the MikroTik device in several ways - through the GUI, and through the device console
Step 2.
Setting up SafeUTM
1. In SafeUTM, open the tab Services -> IPsec -> Devices, click on the icon (+), and fill in the following fields:
- Connection name – specify an arbitrary name for the connection. Maximum 42 characters.
- Connection type – select Incoming, since the connection to UTM is being made.
- Authentication type – select the PSK type.
- PSK – insert the PSK key received from MikroTik.
- Remote side identifier – insert the MikroTik ID (Key ID parameter in
/ip ipsec peers). - Home local network – list all UTM LANs that will be available in an IPsec connection, i.e. will be visible to the opposite side.
- Remote local networks – list all MikroTik LANs that will be available in an IPsec connection, i.e. will be visible to the opposite side.
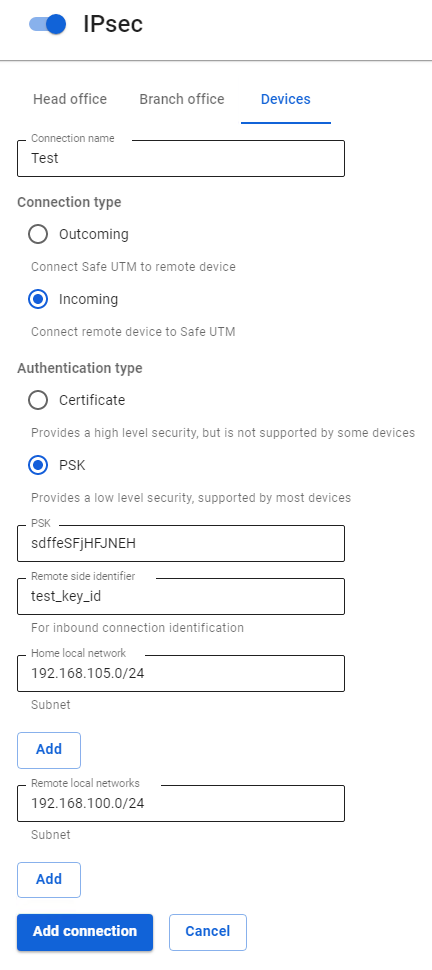
2. After filling in all the fields, click Add connection. Your connection will appear in the list of connections.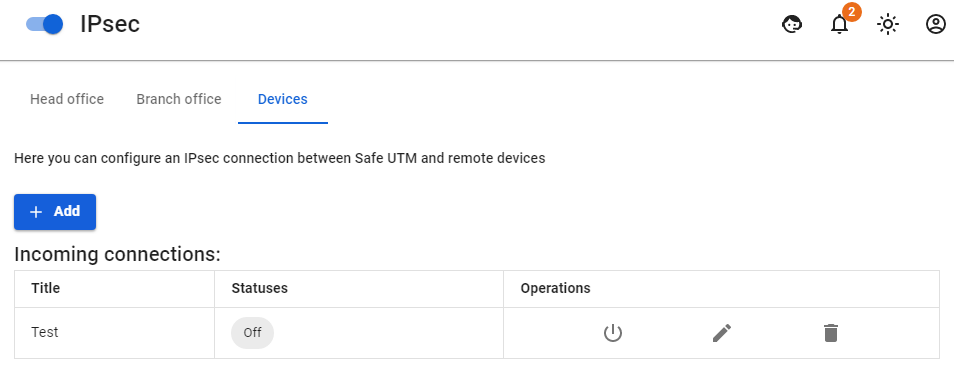
Connecting SafeUTM to MikroTik Using Certificates
Connection with certificates is used because it is more secure than a PSK connection, or in cases when the device does not support PSK.
For the correct operation of certificate connections, it is necessary that the time on MikroTik be synchronized via NTP. To do this, it is sufficient for the device to have access to the Internet.
The creation of outgoing IPsec connections using certificates to MikroTik below version 6.45 does not work due to the inability to use modern crypto algorithms in certificates.
Step 1.
Setting up SafeUTM
1. In SafeUTM, open the tab Services -> IPsec -> Devices, click on the icon (+), and fill in the following fields:
- Connection name – specify an arbitrary name for the connection. Maximum 42 characters.
- Connection type – select Outcoming, because the connection is made from UTM.
- Authentication type – specify the type of Certificate.
- Address of the remote device – specify the external IP address of MikroTik.
- Certificate signing request – a request will be generated which must be sent to MikroTik for signing.
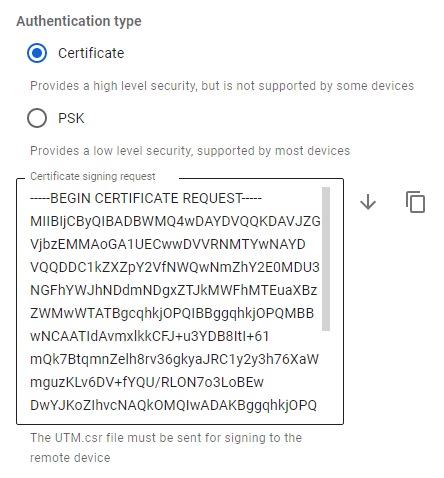
2. After the request is signed, you will need to continue configuring the connection in SafeUTM.
Do not close the settings tab!
Step 2.
Setting up MikroTik
At this stage, you should configure MikroTik to continue configuring UTM.
The UTM.csr file obtained from SafeUTM must be uploaded to the MikroTik file storage. To do this, open the File section, click Browse, select the file and upload it.
You can configure MikroTik in several ways - through the GUI, and through the device console.
Two files will appear in the MikroTik file system which you need to download in order to upload to UTM later.
The file of the type cert_export_device_<random character set>.ipsec.crt is a signed UTM certificate. The file of the type cert_export_mk_ca.crt is the root certificate of MikroTik.
At this point, the MikroTik setup can be considered complete.
Step 3.
Finishing up the SafeUTM setup
Go back to SafeUTM to the tab with the device connection settings and continue filling in the following fields:
- Signed UTM certificate – upload a signed UTM certificate to MikroTik.
- Remote Device Root Certificate – download the MikroTik root certificate.
- Home local networks – list all UTM LANs that will be available in an IPsec connection, i.e. will be visible to the opposite side.
- Remote local networks – list all MikroTik local networks that will be available in an IPsec connection, i.e. will be visible to the opposite side.
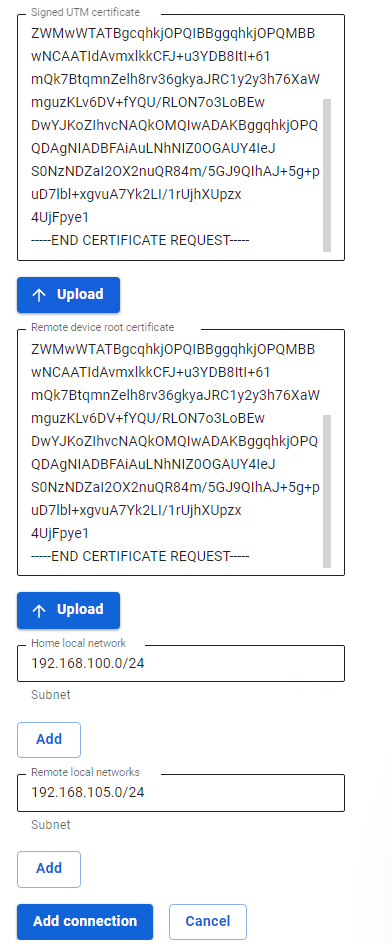
After filling in the fields, click Add connection. Your connection will appear in the list of connections.
Connecting MikroTik to SafeUTM by certificates
Connection with certificates is used because it is more secure than a PSK connection, or in cases when the device does not support PSK.
For the correct operation of certificate connections, it is necessary that the time on MikroTik be synchronized via NTP. To do this, it is sufficient for the device to have access to the Internet.
Step 1.
Setting up MikroTik
You can configure MikroTik in several ways - through the GUI, and through the device console.
Two files will appear in the MikroTik file storage which must be downloaded since they are required for further configuration.:
- File
certificate-request.pemis a certificate signing request. - File
certificate-request_key.pemis a private key.
Next, you will need to fill in the Certificate Signing Request field in SafeUTM, here is how to configure it.
Step 2.
Setting up SafeUTM
1. In SafeUTM, open the tab Services -> IPsec -> Devices, click on the icon (+), and fill in the following fields:
- Connection name – specify an arbitrary name for the connection. Maximum 42 characters.
- Connection type – select Incoming, since the connection to UTM is being made.
- Authentication type – select the type Certificate.
- Certificate Signing Request - Upload the signature request received from MikroTik.
- Home local network – it is necessary to list all UTM LANs that will be available in an IPsec connection, i.e. they will be visible to the opposite side.
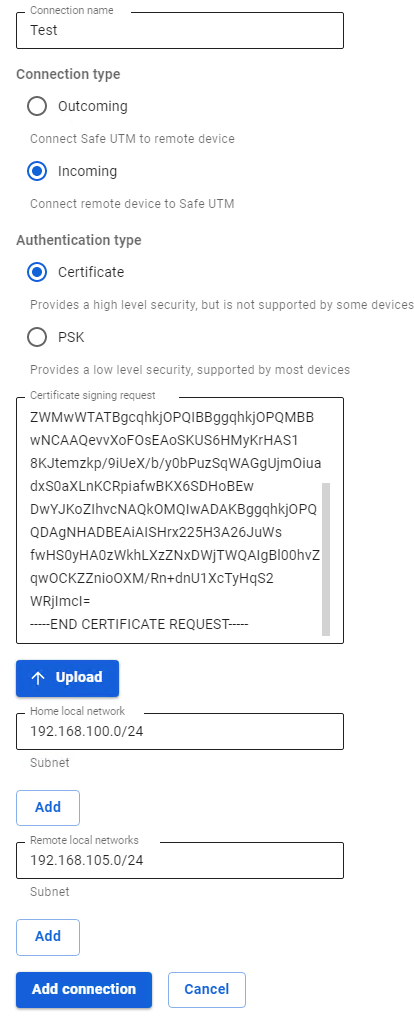
2. After the settings, click Add connection. Your connection will appear in the list of connections. Click on the edit connection button to continue the setup.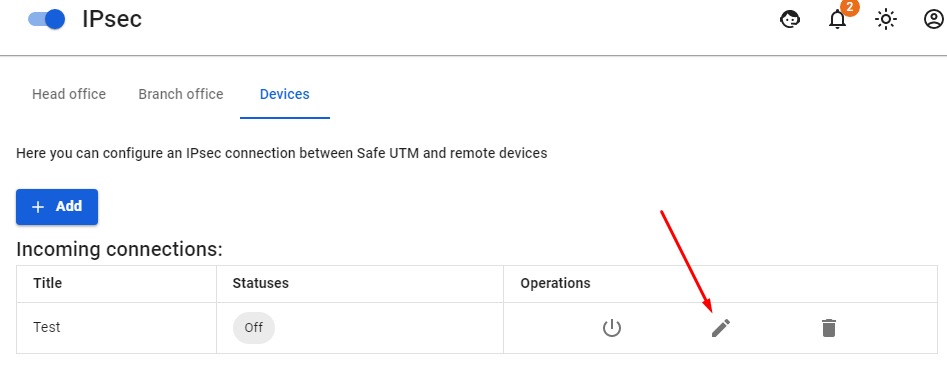
3. The connection settings editing area will appear. You need to download the files that are in the fields UTM root certificate and Signed device certificate for their subsequent use in MikroTik.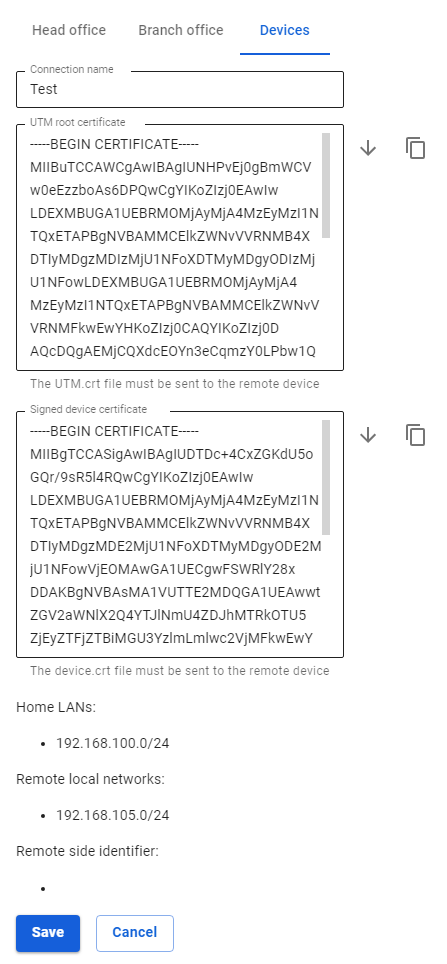
Problems when reactivating an incoming connection to SafeUTM
If after using this connection you turned it off, for example, as unnecessary, and when trying to re-enable the connection failed to be established, then most likely the remote device got into fail2ban (a tool that tracks attempts to access services in log files, and if it finds repeated unsuccessful authorization attempts from the same IP-address or host, it blocks further attempts).
Connecting Mikrotik to SafeUTM via L2TP/IPsec
Configure the connection by running the following commands:
- Edit the IPsec profile:
ip ipsec profile set default hash-algorithm=sha1 enc-algorithm=aes-256 dh-group=modp2048
- Edit IPsec proposals:
ip ipsec proposal set default auth-algorithms=sha1 enc-algorithms=aes-256-cbc,aes-192-cbc,aes-128-cbc pfs-group=modp2048
- Create a connection to SafeUTM:
interface l2tp-client add connect-to={server} profile=default disabled=no name={interface_name} password="{password}" user="{login}" use-ipsec="yes" ipsec-secret="{psk}"